Security Policy Approvals
Why automate?
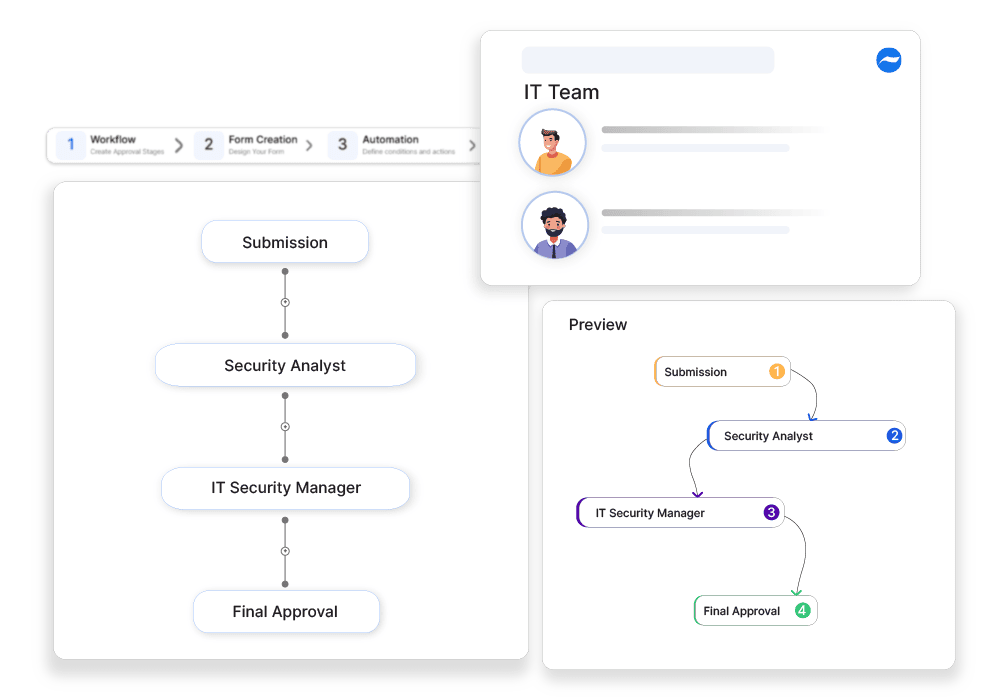
How Cflow Can Help Automate the Process:
Comprehensive Policy Submission:
Cflow provides customizable forms for submitting security policies, capturing all necessary details such as policy objectives, scope, and compliance requirements. This standardization facilitates a comprehensive review process.
Efficient Policy Implementation:
Once approved, Cflow can integrate with security management tools to automate the implementation of security policies. This reduces the time taken to enforce policies and ensures that security measures are applied accurately and securely.
Audit and Compliance Reporting:
Cflow maintains a detailed audit trail of all security policy approvals and actions taken. This helps organizations monitor security activities, ensure compliance with regulations, and quickly identify any issues.
Automated Review and Approval Workflow:
Cflow routes security policies to relevant stakeholders for review and approval. This ensures that each policy is thoroughly evaluated by the appropriate personnel, reducing the risk of oversights and ensuring comprehensive evaluations.
Frequently Asked Questions
What should a strong IT security policy include?
Access control rules, data encryption requirements, and incident response protocols.
How can organizations ensure security policy compliance?
By conducting regular audits and employee security training.
What are the consequences of weak security policies?
Increased risk of cyberattacks, data breaches, and compliance violations.



