Penetration Test Scheduling
Why automate?
How Cflow Helps:
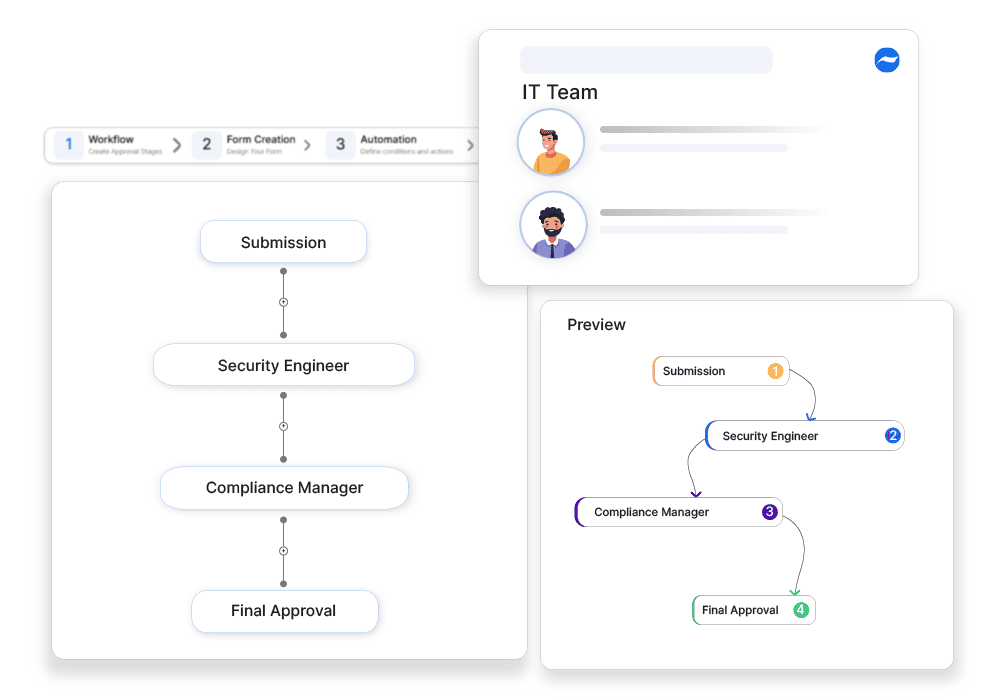
Structured Pen Test Request Approvals
Cflow routes penetration test requests to designated security teams for approval, ensuring tests are authorized before execution.
Risk-Based Test Scheduling
High-risk tests require additional approval layers, while routine security scans can be automatically approved based on predefined rules.
Conflict-Free Scheduling
Cflow ensures that penetration tests do not interfere with production systems or critical business operations by coordinating schedules with IT teams.
Test Execution Documentation
Every approved penetration test is logged, time-stamped, and stored for audit purposes, ensuring security teams can track historical test data.
Frequently Asked Questions
What is penetration test scheduling?
The process of coordinating security assessments to simulate cyberattacks on systems.
What are the main challenges?
Testing overlaps, business disruption risks, and third-party coordination.
How can it be improved?
By maintaining a centralized test calendar and aligning schedules with system owners.



