Container Image Vulnerability Scans
Why automate?
How Cflow Helps:
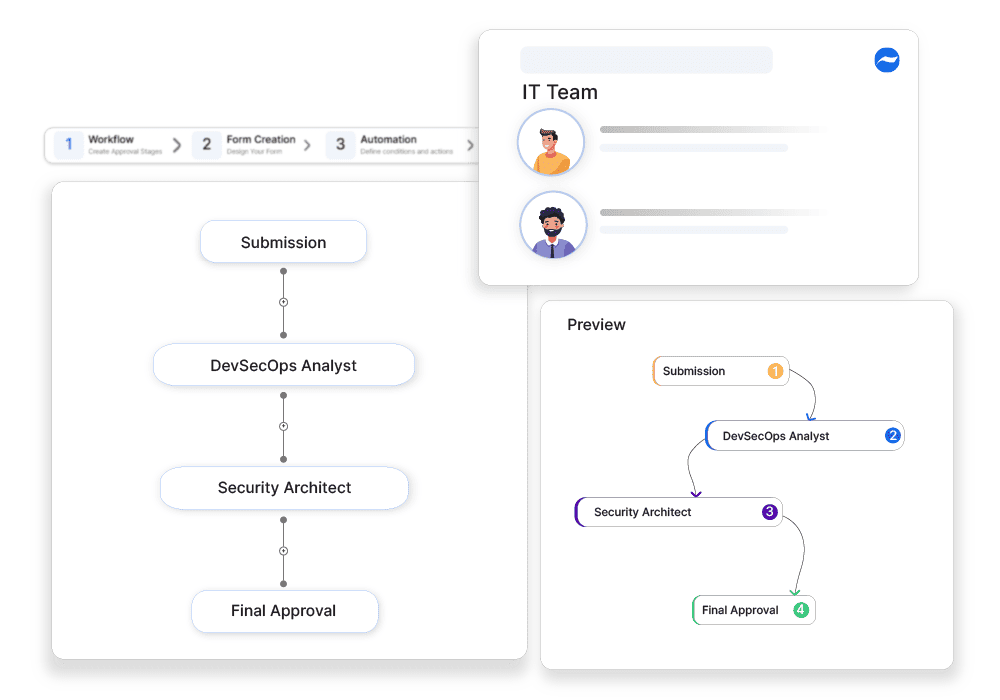
Structured Vulnerability Scan Approvals
Cflow routes scan results for review and approval, ensuring that high-risk vulnerabilities are addressed before deployment.
Escalation for Critical Findings
For severe vulnerabilities, Cflow triggers automated escalation workflows, ensuring that security teams act immediately.
Compliance Enforcement for Secure Deployments
Cflow ensures that only approved, vulnerability-free container images move into production, maintaining security compliance.
Historical Scan Review Logs
Cflow maintains a record of all approved and rejected scans, allowing teams to track security trends and refine policies.
Frequently Asked Questions
What are container image vulnerability scans?
Security checks that identify flaws or exploits in container images before deployment.
What are the main challenges?
Unscanned images, outdated libraries, and delayed remediation.
How can this process be improved?
By automating scans in CI/CD and enforcing policy compliance before deployment.



