Application Access Requests
Why automate?
How Cflow Can Help Automate the Process:
Centralized Request Submission:
Cflow provides customizable forms for submitting application access requests, capturing essential details such as the purpose of access, required applications, and user information. This standardization ensures that all relevant information is collected upfront.
Secure Access Provisioning:
Once approved, Cflow integrates with access management systems to automate the provisioning of application access. This minimizes the time taken to grant access and ensures that permissions are configured accurately.
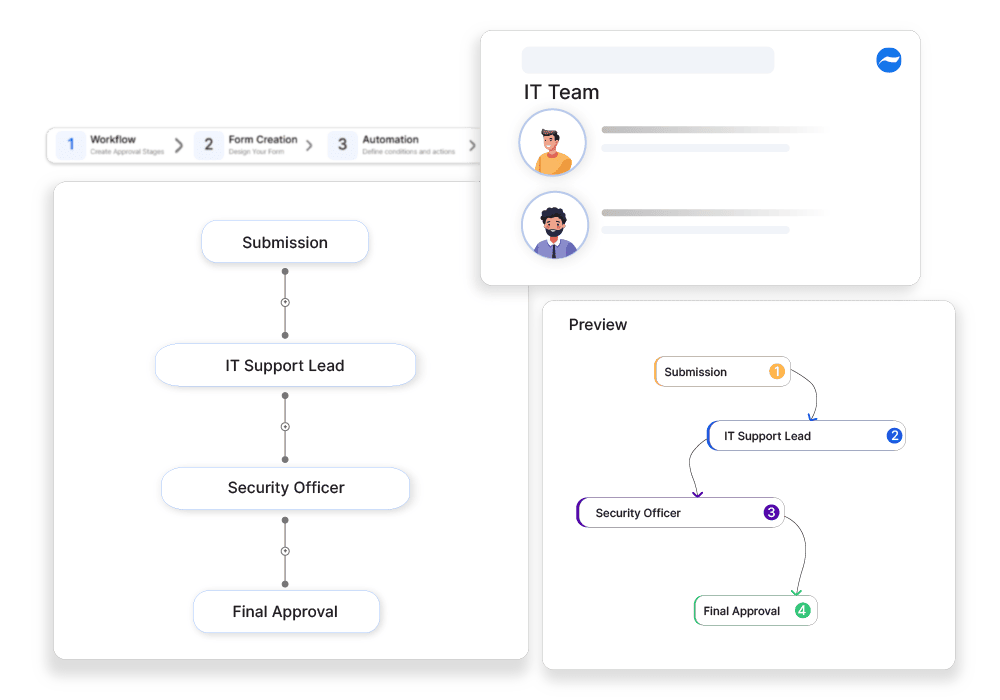
Automated Approval Workflow:
Cflow routes application access requests to relevant stakeholders for review and approval. This ensures that each request is evaluated by the appropriate personnel, maintaining security and compliance.
Audit and Compliance Reporting:
With Cflow, IT teams can maintain an accurate and updated audit trail of all app access requests and their processing. This helps organizations monitor access activities, ensure compliance with security policies, and quickly identify any unauthorized access attempts.
Frequently Asked Questions
1. What are the common reasons for an application access request to be denied?
Access requests may be denied due to insufficient authorization, security policy restrictions, or incorrect user roles assigned.
2. How long does it take for an application access request to be approved?
Approval times vary based on the workflow complexity and the approver’s availability, but most requests are processed within 24 to 48 hours.
3. What should I do if my application access request is delayed?
You can follow up with the approving manager or IT department, ensuring all required details are correctly submitted to avoid further delays.



