System Log Monitoring Requests
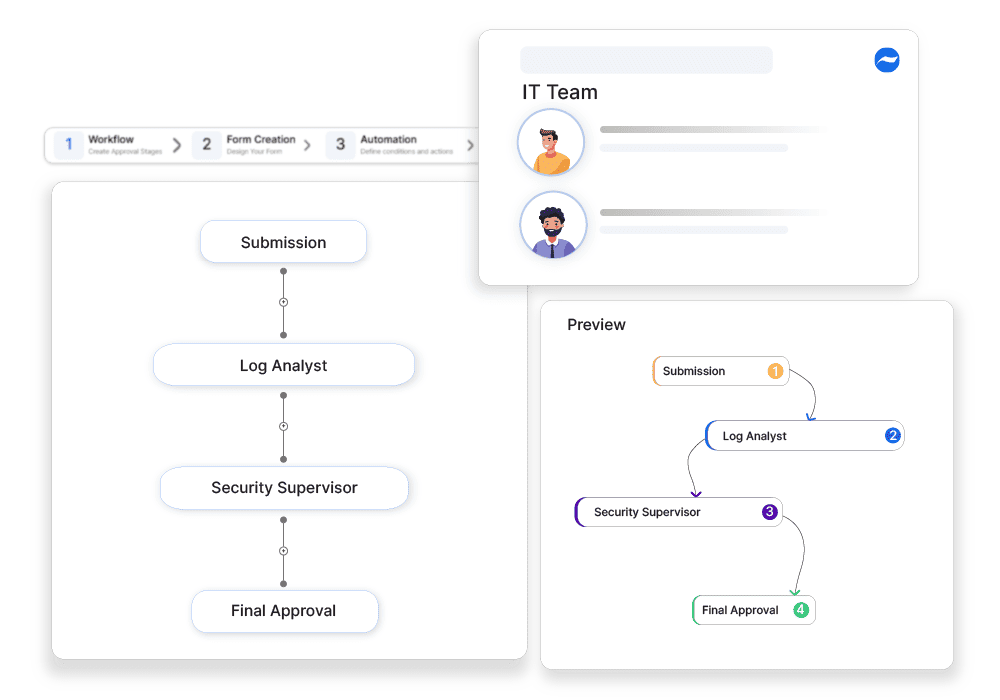
Why automate?
How Cflow Helps:
Controlled Log Access Approvals
Cflow ensures that log access requests are reviewed and approved by security teams, preventing unauthorized monitoring.
Faster Response to Security Alerts
Cflow routes urgent log review requests for immediate approval, helping IT teams detect and respond to anomalies faster.
Audit-Ready Approval Records
Cflow maintains a complete log of all access approvals, ensuring compliance with security and regulatory policies.
Scheduled Log Monitoring Requests
Cflow allows IT teams to set up recurring log review approvals, ensuring continuous monitoring without manual intervention.
Frequently Asked Questions
What is a system log monitoring request?
A request to review and analyze system logs for security and performance issues.
What are the main challenges in system log monitoring requests?
Large log volumes, delayed analysis, and lack of actionable insights.
How can businesses streamline system log monitoring requests?
By using log aggregation tools, setting automated alerts, and defining log review schedules.



