Software Dependency Vulnerability Management Workflow
Automate software dependency vulnerability approvals to enhance security and ensure compliance.
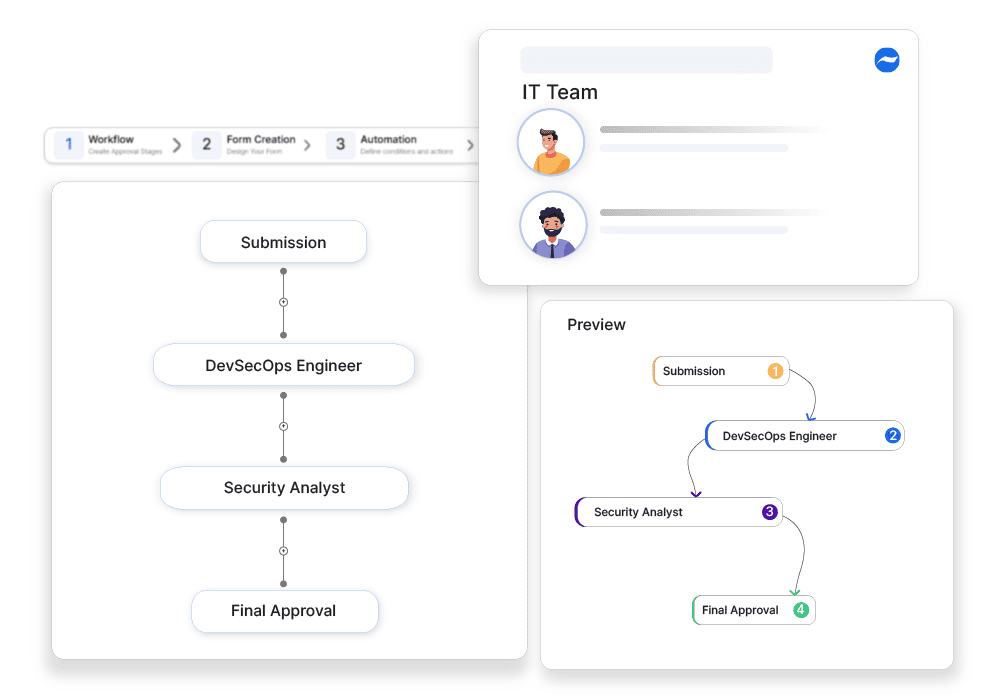
Why automate?
Software dependencies can introduce security risks if vulnerabilities exist in third-party libraries, frameworks, or modules. Managing dependency updates ensures applications remain secure and compliant with industry standards. Without structured approvals, unverified dependency updates may introduce compatibility issues, unpatched security flaws, or licensing violations. Manual processes delay vulnerability mitigation, increasing the risk of cyber threats. Cflow helps to automate Software Dependency Vulnerability Management Approvals, ensuring that dependency updates are reviewed, approved, and implemented securely, reducing risks and maintaining software integrity.
How Cflow Helps:
Approval-Based Vulnerability Fixes
Cflow ensures that all dependency updates follow structured approvals, preventing untested patches.
Compliance with Security Frameworks
Approved updates align with OWASP, NIST, and industry best practices, reducing risk exposure.
Faster Vulnerability Mitigation
Critical patches receive priority approvals, ensuring immediate security fixes.
Full Audit Trail for Dependency Updates
Cflow logs all approved dependency changes, providing transparency in security management.
Frequently Asked Questions
What is software dependency vulnerability management?
A process to detect and address security vulnerabilities in third-party libraries and dependencies.
What are the main challenges?
Outdated libraries, unnoticed vulnerabilities, and patching delays.
How can it be optimized?
By integrating dependency scanners in CI/CD and automating patch updates.



