Understanding Audit Trails: Why are they Important for Transparency and Compliance in Business Operations

Key takeaways
- An audit trail provides a chronological record of user actions, transactions, and changes across systems to ensure transparency and accountability.
- Audit trails are essential for regulatory compliance in industries like finance, healthcare, and legal, helping organizations demonstrate secure and compliant operations.
- Secure audit trails include time-stamps, user identification, tamper-proof storage, and clear documentation of each activity performed.
- Real-world applications include financial transaction tracking, IT system access logs, and employee onboarding approvals—all helping to reduce risk and maintain data integrity.
- Implementing audit trail software enables centralized monitoring, real-time alerts, and automated reporting for better governance and faster issue resolution.
Table of Contents
What is an Audit Trail?
An audit trail refers to the systematic documentation of events, transactions, or activities that occur within a system, process, or workflow. It captures who did what, when it was done, and how it was carried out—creating a time-stamped record that helps organizations ensure accountability, traceability, and compliance.
Whether it’s financial transactions, software system changes, or access logs in an IT environment, audit trails provide a detailed log that can be reviewed, verified, and validated as needed.
In modern businesses, audit trails are essential for internal governance, external regulatory compliance, and operational integrity. They help prevent fraud, ensure that policies are followed, and simplify investigations when discrepancies occur.
By maintaining an accurate, tamper-proof log of all activities, organizations can not only build trust but also improve performance and decision-making.
In this blog, we’ll explore why audit trails are important, how they help in compliance audits, the components of a secure audit trail, real-world examples, implementation strategies, and the benefits of using audit trail software.
Why are Audit Trails Important in Business Operations?
Audit trails play a critical role in ensuring transparency and control across all business functions. They serve as a digital footprint of internal operations, capturing actions performed by users, applications, or systems. This helps business leaders maintain operational oversight and ensure procedures are being followed as intended.
For instance, in financial reporting, audit trails can trace every step of a transaction from initiation to completion, allowing finance teams to verify data accuracy and trace any anomalies. In IT environments, audit trails help track system changes, unauthorized access attempts, or failed login attempts, making it easier to detect security threats or data breaches.
Additionally, audit trails act as an invaluable tool during internal or external audits. Auditors can quickly examine how processes were executed and determine if they adhered to company policies and industry regulations. With detailed audit logs, companies can easily identify bottlenecks, unauthorized changes, or compliance violations, and take corrective action.
By providing a verifiable history of actions, audit trails help businesses mitigate risks, enhance data governance, and improve accountability at all levels.
How do Audit Trails Help in Compliance Audits?
Regulatory compliance is a major driver for maintaining comprehensive audit trails in today’s business environment. Industries such as healthcare, finance, legal, and manufacturing are governed by strict regulatory frameworks that require organizations to maintain records of all user activity, data access, and process changes.
In compliance audits, regulators typically ask for evidence that certain actions were completed, reviewed, and approved according to policy. This is where audit trails prove indispensable. They offer time-stamped documentation that shows when a task was performed, who did it, and what data was affected.
For example, in the healthcare sector, regulations like HIPAA mandate that organizations must monitor access to patient records and ensure only authorized personnel have access. An audit trail provides the necessary documentation to demonstrate compliance and avoid penalties. In finance, regulations such as SOX (Sarbanes-Oxley) require audit trails for financial transactions, controls, and reporting processes to prevent fraud and ensure transparency.
Without a reliable audit trail, businesses face challenges in proving compliance, may fail audits, and expose themselves to legal and financial risks. Implementing a robust audit trail system helps organizations remain audit-ready at all times.
What are the Key Components of a Secure Audit Trail?
For an audit trail to serve its purpose effectively, it must be designed with both operational accuracy and security in mind. A secure audit trail is not simply a list of events—it is a structured, tamper-resistant, and transparent record of activities that offers legal, regulatory, and operational value.
Each component of the audit trail plays a crucial role in ensuring that the data it captures is credible, verifiable, and usable for decision-making, investigations, or compliance audits.
1. Time-stamping every event
Time-stamping is one of the most essential features of a secure audit trail. Every action or transaction must be recorded with an exact date and time down to the second. This allows organizations to reconstruct the timeline of events in a precise and orderly manner.
Whether it’s a failed login attempt or a critical configuration change, knowing exactly when it happened is crucial in diagnosing problems, identifying security incidents, or demonstrating compliance. Accurate timestamps also enable audit logs to be synchronized across systems and correlated with other monitoring tools, improving visibility and control.
2. User identification and role association
Each log entry should identify the user or system account responsible for the action. This includes capturing user IDs, IP addresses, role assignments, and—where applicable—device information. This level of detail supports accountability by linking every activity to a specific individual or process.
If unauthorized access, data leakage, or fraudulent activity is suspected, a reliable audit trail allows organizations to pinpoint the source immediately. Moreover, for environments governed by compliance regulations, such as HIPAA or SOX, being able to prove exactly who did what is a non-negotiable requirement.
3. Detailed activity logging
Beyond knowing when and who, a secure audit trail must document what happened. Each record should describe the nature of the activity being performed, such as a login event, record update, file deletion, or policy approval. This helps auditors and security personnel understand the context of the action.
For example, in financial workflows, a modification to a payment amount should not only log the user but also the old and new values, reasons for the change, and the step in the approval process. This level of granularity supports transparency and reduces the risk of misinterpretation.
4. Tamper-proof and immutable storage
Security is at the heart of a trustworthy audit trail. If logs can be altered after the fact, their value as an audit or forensic tool is diminished. Secure audit trails must be protected from tampering through encryption, role-based access control, and immutable storage formats such as WORM (Write Once Read Many).
Some modern systems even use blockchain or cryptographic hashing to ensure every entry is permanently locked in sequence and cannot be changed without detection. By ensuring immutability, businesses guarantee that their audit records are legally defensible and technically reliable.
5. Searchability and exportability
An audit trail is only useful if it can be accessed, reviewed, and analyzed efficiently. That’s why searchability is a vital component. Users should be able to filter logs based on dates, user IDs, activity types, or affected resources.
Exportable reports also make it easier to share logs with auditors, legal teams, or management during reviews. The ability to extract relevant portions of the audit trail without exposing sensitive unrelated data is essential for maintaining both efficiency and data privacy.
6. Data retention and archival policies
A complete audit trail strategy also involves determining how long logs are stored and how they are archived. Retention policies should align with legal, industry, and organizational requirements.
Some industries require records to be preserved for multiple years, especially in financial services and healthcare. Secure archival systems ensure that old records are still accessible when needed, even if the system has evolved or been replaced.
7. Integration with monitoring and incident response
An audit trail should not operate in isolation. To be most effective, it should integrate with your broader IT infrastructure, including security information and event management (SIEM) systems, workflow automation platforms, and incident response tools. This enables real-time monitoring, automated alerting, and faster incident resolution. When audit trails work in tandem with other controls, they become an active part of your risk management and operational intelligence strategy.
By ensuring that these key components are present and functioning properly, businesses can rely on their audit trails to provide robust protection, support internal governance, meet compliance mandates, and respond quickly to any irregularities or threats. A secure, detailed, and accessible audit trail is not just a safety net—it’s a strategic asset for modern digital organizations.
Real-World Examples of Audit Trails in Financial Systems
In the financial industry, where accuracy, accountability, and compliance are non-negotiable, audit trails serve as a cornerstone of effective financial management. They provide a transparent log of all activities that occur within financial systems, ensuring that every transaction, approval, and adjustment is fully traceable. From daily operations to regulatory audits, audit trails help organizations maintain control and build trust with stakeholders.
1. Accounts Payable and Vendor Payments
One of the most common applications of audit trails in finance is within the accounts payable (AP) process. Every invoice that enters the system must pass through multiple layers of approval, starting from validation, moving through budget checks, and ending in final payment authorization.
An audit trail records each stage of this process: when the invoice was received, who reviewed and approved it, any modifications made (such as adjusting payment terms or correcting vendor details), and the date the payment was issued.
In cases where disputes arise with vendors or internal finance teams, these logs provide clarity. They show exactly when the issue occurred, what action was taken, and by whom. This prevents finger-pointing and accelerates resolution.
2. Budget Approvals and Adjustments
Corporate budgeting is another area where audit trails play a critical role. Department heads often request changes to their allocated budgets due to operational needs or unforeseen expenses. The audit trail captures every aspect of this process: the original budget, requested revisions, comments or justifications provided, approvals obtained, and final adjustments.
This level of documentation prevents unauthorized spending and ensures that budget decisions align with organizational priorities and internal policies.
It also provides finance leaders with the ability to look back over historical changes during audits or strategic planning, offering insight into recurring trends or deviations.
3. Customer Banking Transactions
In banking systems, audit trails are used to monitor all customer interactions and system activities. This includes logins, balance inquiries, fund transfers, ATM withdrawals, online banking updates, and mobile app usage. Each action is time-stamped and associated with a customer ID, device, or IP address.
In the event of suspected fraud or account compromise, these logs help investigators reconstruct the timeline of suspicious activity. Was the login from an unfamiliar location? Were multiple password attempts made? Did a large transfer occur shortly after a password reset? These questions can be answered definitively through a detailed audit trail.
Moreover, audit trails assist banks in fulfilling anti-money laundering (AML) and know your customer (KYC) compliance requirements, where traceability of financial transactions is legally mandated.
4. Internal Financial Controls and Reconciliation
Financial reconciliation, whether daily or monthly, involves comparing ledger entries with bank statements, expense reports, or internal balances. If discrepancies are found, auditors or accountants rely on audit trails to determine the root cause. Was an entry posted twice? Did someone amend a transaction date? Was there a delay in recording a payment?
The audit trail helps pinpoint exactly where and why mismatches occur, enabling finance teams to correct errors quickly and with documented evidence. This reduces the risk of misstatements in financial reporting and supports accuracy in closing processes.
5. Investment and Trading Platforms
For firms operating in capital markets or investment management, audit trails help track trades, portfolio adjustments, and client instructions. A record of who initiated a trade, the asset details, execution time, and final confirmation ensures transparency and compliance with regulations such as SEC Rule 17a-4.
In cases of market anomalies or client disputes, these logs become invaluable for reconstructing activity and proving that trades were executed according to policy and client consent.
6. Expense Reimbursement and Corporate Credit Cards
Organizations with employee expense policies benefit from audit trails when managing reimbursement requests or corporate card usage. Audit logs capture expense submissions, receipts uploaded, policy violations flagged by the system, and final approval by supervisors or finance managers.
In audits or internal reviews, finance teams can pull up logs to verify whether claims were processed correctly and according to policy. This protects against fraudulent claims and ensures equitable application of financial controls.
7. Regulatory Reporting and Financial Compliance
Perhaps most importantly, audit trails in financial systems simplify the regulatory reporting process. Whether you’re dealing with tax authorities, compliance bodies, or internal audit teams, having a digital trail of every financial action makes it easier to generate reports, validate entries, and respond to queries without relying on manual reconciliation or anecdotal evidence.
Institutions that are publicly traded or operate across multiple jurisdictions must meet rigorous standards for data traceability and financial governance. A comprehensive audit trail serves as both a compliance tool and a safeguard against reputational or legal risks.
In summary, audit trails in financial systems do more than just capture transactions—they create a framework for trust, integrity, and operational excellence. They empower finance teams to maintain transparency, resolve conflicts efficiently, and make informed decisions based on verifiable data. Whether you’re processing payments, adjusting budgets, or responding to an audit, a secure and searchable audit trail is your strongest ally.
End-to-end workflow automation
Build fully-customizable, no code process workflows in a jiffy.
Benefits of Maintaining an Audit Trail
Maintaining an audit trail provides numerous benefits that go beyond compliance and security. First, it strengthens internal controls by making every action traceable. Employees and system users are more likely to follow policies when they know their activities are being monitored and recorded.
Audit trails also enhance data accuracy. When users know changes are being logged, it reduces the likelihood of careless errors, unauthorized edits, or missing records. In turn, this builds confidence in the integrity of your systems and reports.
Another key benefit is operational efficiency. Audit trails make it easier to detect process inefficiencies, such as recurring delays in approval cycles or frequent data rework. Managers can use this insight to fine-tune workflows and reduce bottlenecks.
Audit logs also play a critical role in incident response. In the event of a data breach, cyberattack, or system failure, audit trails provide investigators with the evidence needed to identify the source, assess the damage, and take corrective action.
Overall, audit trails support business continuity, risk management, and performance improvement by offering a clear view into how work is performed and decisions are made.
How to Implement an Audit Trail System in Your Organization
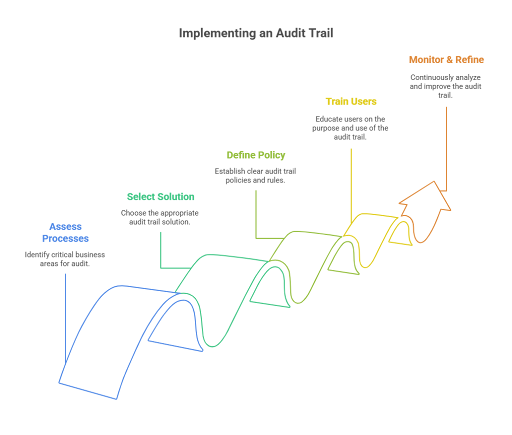
Successfully implementing an audit trail system requires a strategic approach that balances technology, policy, and culture. An effective audit trail should be integrated seamlessly into your existing operations while aligning with compliance obligations and risk management goals. Here are the key steps to follow:
1. Assess business processes and identify critical areas
Begin by analyzing your current business workflows to determine which ones require the highest level of visibility and traceability. Focus on areas that deal with sensitive data, financial transactions, client records, regulatory reporting, or system access. These typically include departments like finance, HR, IT, procurement, and customer service.
During this phase, document who performs what tasks, where handoffs occur, and what systems are used. Identifying pain points—such as repeated errors, approval delays, or compliance gaps—will help you prioritize which processes need immediate audit trail coverage.
2. Select the right audit trail solution
Choose a technology platform that integrates easily with your current software ecosystem—whether it’s ERP systems like SAP, HR software such as Workday, CRM platforms like Salesforce, or workflow tools like Cflow. Look for solutions that offer real-time activity logging, customizable data fields, access controls, and immutable storage to prevent tampering.
The platform should also support centralized data monitoring, meaning it can aggregate logs from different sources and present them in a unified dashboard. Consider whether the solution can scale with your business, support cloud environments, and comply with relevant regulations such as GDPR, HIPAA, or SOX.
3. Define your audit trail policy and governance rules
Once you’ve selected a tool, it’s critical to develop a clear and enforceable audit trail policy. This policy should outline:
- Which actions are logged: Identify specific events to capture, such as logins, record edits, file uploads, approvals, deletions, or system configurations.
- Who is responsible: Define ownership for maintaining and reviewing audit logs. Assign roles and permissions to control who can view, manage, or extract audit trail data.
- How long data is retained: Establish retention periods based on industry regulations and organizational needs. Some industries require logs to be stored for 7+ years.
- Data protection measures: Ensure that logs are encrypted, access-controlled, and protected from unauthorized alteration.
Having a documented policy creates consistency across departments and makes it easier to demonstrate compliance during audits.
4. Train users and communicate the purpose
The success of an audit trail system depends heavily on user adoption and understanding. Conduct training sessions to explain how the system works, what actions are tracked, and why it’s being implemented. Emphasize that the goal is not surveillance, but rather transparency, accountability, and operational improvement.
Training should be tailored by role—for instance, IT admins may need deeper technical knowledge, while end users may only need to understand how their actions are recorded. Create guides, FAQs, and internal communications that reinforce positive messaging and build trust in the system.
5. Monitor, analyze, and refine continuously
Implementation doesn’t end once the system goes live. Schedule regular reviews of your audit trail data to uncover unusual patterns, security threats, or operational inefficiencies. Use audit trail analytics to identify bottlenecks—such as repeated approval delays or frequent policy violations that need attention.
Set up automated alerts for critical events, like unauthorized access attempts or failed transactions. Use dashboards to track trends over time and report key findings to leadership or compliance teams.
Additionally, revisit your audit trail policy annually to reflect changes in business processes, technology, or regulations. As your organization evolves, your audit trail strategy should adapt to ensure continued value and compliance.
By following these steps, organizations can implement a robust audit trail system that not only protects against risk but also improves workflow efficiency, ensures data integrity, and builds a culture of accountability. The right audit trail solution becomes more than a compliance tool—it’s a strategic asset that supports better decision-making and operational excellence.
Benefits of Using Audit Trail Software
Using dedicated audit trail software automates the process of capturing, storing, and analyzing activity logs across the organization. These platforms are designed to handle large volumes of data, ensure data integrity, and provide intuitive dashboards for tracking user actions and process flows.
One major advantage is real-time monitoring. With audit trail software, administrators can instantly see who did what and when, enabling a faster response to issues or irregularities. This is particularly valuable in high-risk environments where unauthorized access or policy violations must be flagged immediately.
Another benefit is centralization. Rather than scattering logs across departments or systems, audit trail software consolidates them in a single location, making it easier to manage, secure, and retrieve data when needed.
These tools also offer automated alerts and reporting, which simplify compliance audits and reduce the manual effort required to prepare documentation. With features like role-based access, encryption, and audit history export, businesses can meet security standards and satisfy auditor demands with confidence.
Investing in audit trail software is a proactive step toward building a more accountable, transparent, and secure business environment.
Maintaining an Audit Trail with Cflow
Cflow is a powerful no-code workflow automation platform designed to help organizations implement secure, scalable, and transparent processes, making it an ideal solution for maintaining audit trails across departments. By automatically recording every user action, task update, and workflow change, Cflow offers end-to-end visibility into your business operations. Its audit trail features are embedded into every process you create, eliminating the need for external logging systems or manual recordkeeping.
Cflow’s audit trail functionality is not just about capturing data—it’s about providing actionable insights, ensuring compliance, and enabling continuous improvement. Every workflow in Cflow maintains a detailed, time-stamped history of events, which helps users trace back decisions, verify compliance, and identify inefficiencies with ease.
Key Features in Cflow for Audit Trail Management
- Time-Stamped Activity Logs
Cflow records every action with precise timestamps—capturing when a form was submitted, who approved it, when it was escalated, and when it was completed. This ensures a full chronological record of every process step. - User Identity Tracking
Each action in the workflow is linked to a specific user or role, providing full transparency into who did what. This accountability is vital for internal governance and audit reviews. - Immutable Workflow History
Once recorded, Cflow’s logs cannot be altered or deleted. The audit trail is stored in a secure, tamper-proof format, making it compliant with industry standards and legally defensible during external audits. - Process-Level Audit Trail Reports
Cflow offers built-in reporting that lets users export audit logs for specific processes, users, or timeframes. This simplifies audit preparation and makes it easy to respond to compliance requests. - Role-Based Access Control
Only authorized users can view or access specific audit data. This ensures data privacy while maintaining transparency for those who need it. - Visual Workflow Monitoring
Managers can view a real-time snapshot of any workflow—including current status, pending actions, and past events—without needing to dig through raw log files. - Integration with Cloud and Document Repositories
Cflow integrates seamlessly with cloud storage systems, enabling secure storage of documents and logs while keeping the audit trail intact and easily accessible.
With these features, Cflow allows organizations to maintain a robust and compliant audit trail, enhance process transparency, and reduce the effort required to prepare for audits or investigations.
Conclusion
An effective audit trail is no longer optional—it’s a vital part of maintaining transparency, ensuring regulatory compliance, and building operational trust. From financial workflows and HR processes to IT systems and customer transactions, audit trails provide the accountability businesses need to function securely and efficiently.
Cflow empowers organizations to embed audit trail functionality directly into their workflows, capturing every action, decision, and change with precision and integrity. With real-time tracking, immutable logs, and role-based visibility, Cflow turns audit compliance into a seamless part of your daily operations.
Start building secure, traceable, and compliant workflows today—sign up for a free trial of Cflow and experience the power of workflow automation with built-in audit trails.
What should you do next?
Thanks for reading till the end. Here are 3 ways we can help you automate your business:

Do better workflow automation with Cflow
Create workflows with multiple steps, parallel reviewals. auto approvals, public forms, etc. to save time and cost.

Talk to a workflow expert
Get a 30-min. free consultation with our Workflow expert to optimize your daily tasks.

Get smarter with our workflow resources
Explore our workflow automation blogs, ebooks, and other resources to master workflow automation.

