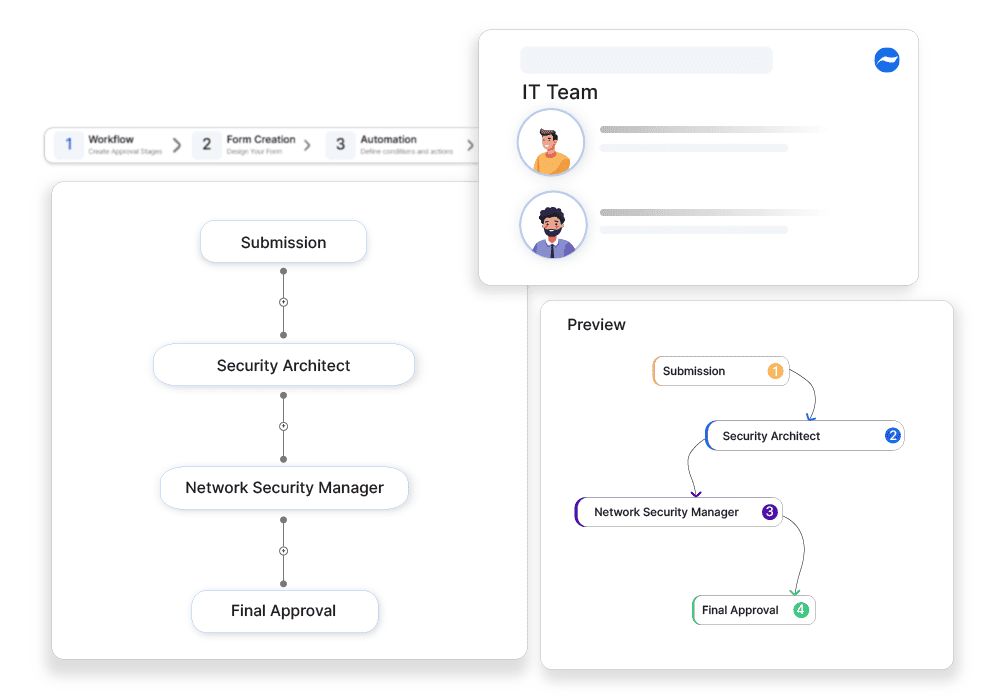
Zero Trust Network Access Control Workflow
Why automate?
How Cflow Helps:
Approval-Driven Network Access Controls
Cflow ensures that all network access requests go through structured approvals, preventing unauthorized access.
Role-Based Access Approvals
Requests are approved based on user roles and security policies, ensuring access is restricted appropriately.
Compliance with Security Standards
Approved access requests align with Zero Trust principles and cybersecurity frameworks.
Full Visibility with Access Logs
Cflow logs all approved access requests, allowing IT teams to track access patterns and security risks.
Frequently Asked Questions
What is a zero trust network access control workflow?
A process that restricts access to resources based on strict identity verification.
What are the main challenges in zero trust access control?
User resistance, complex access policies, and performance issues.
How can businesses streamline zero trust access control?
By implementing role-based access, using MFA, and automating access reviews.



