User Access Review Workflows
Why automate?
How Cflow Helps:
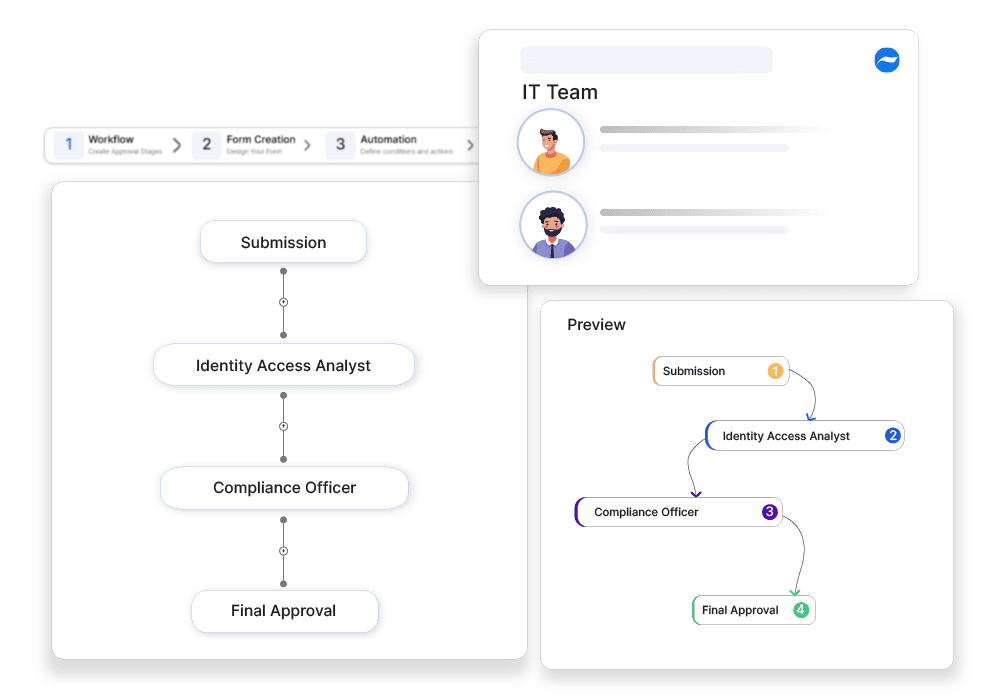
Role-Based Access Review Approvals
Cflow ensures that access requests are reviewed by the right approvers, based on roles, departments, and security policies. Approvals are routed to managers, IT administrators, or compliance officers, ensuring all access changes are properly evaluated.
Scheduled Review Cycles
With Cflow, organizations can set automated review cycles (monthly, quarterly, or annually) to ensure that user permissions remain relevant and compliant. This prevents employees from retaining unnecessary access after role changes or project completion.
Automatic Deactivation for Expired Access
Cflow helps enforce policies by revoking permissions that are no longer needed. If access is not explicitly approved, Cflow can automatically trigger deactivation workflows, ensuring security compliance.
Audit-Ready Logs for Compliance
Every approval or rejection is logged and time-stamped, creating a transparent audit trail. This ensures that IT teams can demonstrate compliance with regulatory requirements and easily review historical access records when needed.
Frequently Asked Questions
What is a user access review?
A periodic check to validate that users have appropriate access levels for their roles.
What are the main challenges?
Manual reviews, missed permissions, and compliance gaps.
How can the process be improved?
By automating user-role mapping, integrating with identity providers, and scheduling regular reviews.



