Threat Modeling and Risk Mitigation Workflow
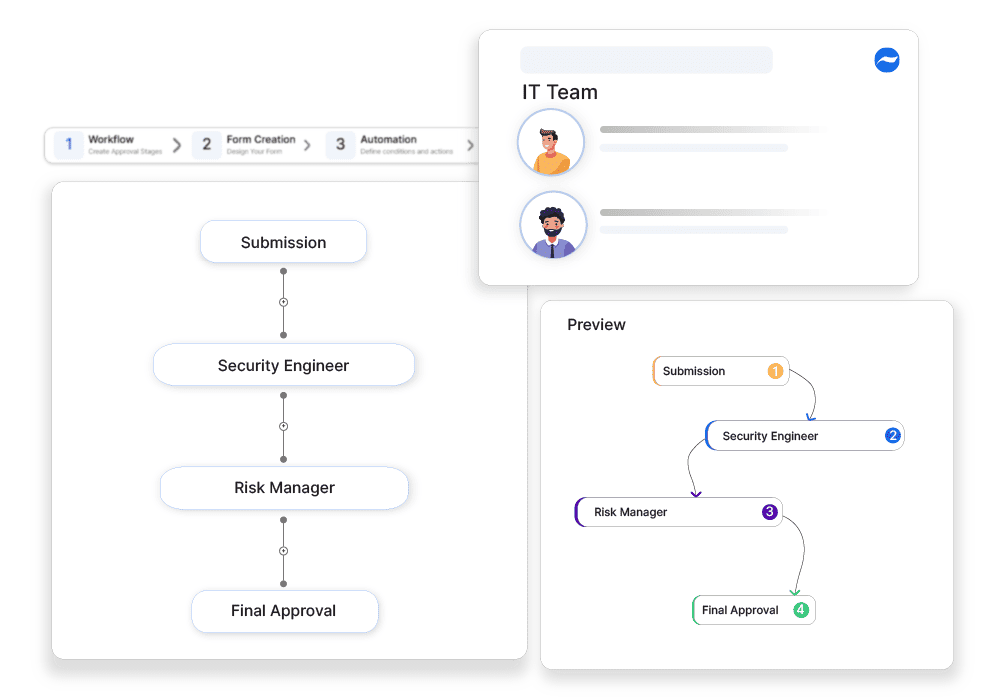
Why automate?
How Cflow Helps:
Approval-Based Security Risk Reviews
Cflow ensures that all risk assessments follow structured approvals, preventing oversight.
Compliance with Cybersecurity Standards
Approved threat models align with MITRE ATT&CK, NIST, and industry best practices, ensuring security readiness.
Prioritized Mitigation Plans
Critical threats receive priority approvals, ensuring proactive risk mitigation.
Full Audit Trail for Threat Analysis
Cflow logs all approved risk mitigation strategies, providing visibility into security decisions.
Frequently Asked Questions
What is a threat modeling and risk mitigation workflow?
A process for identifying potential security threats and defining mitigation strategies.
What are the main challenges in threat modeling and risk mitigation?
Incomplete threat identification, lack of mitigation plans, and inconsistent execution.
How can businesses streamline threat modeling and risk mitigation?
By using threat modeling tools, defining risk categories, and automating mitigation steps.



