Data Privacy Compliance Checks
Why automate?
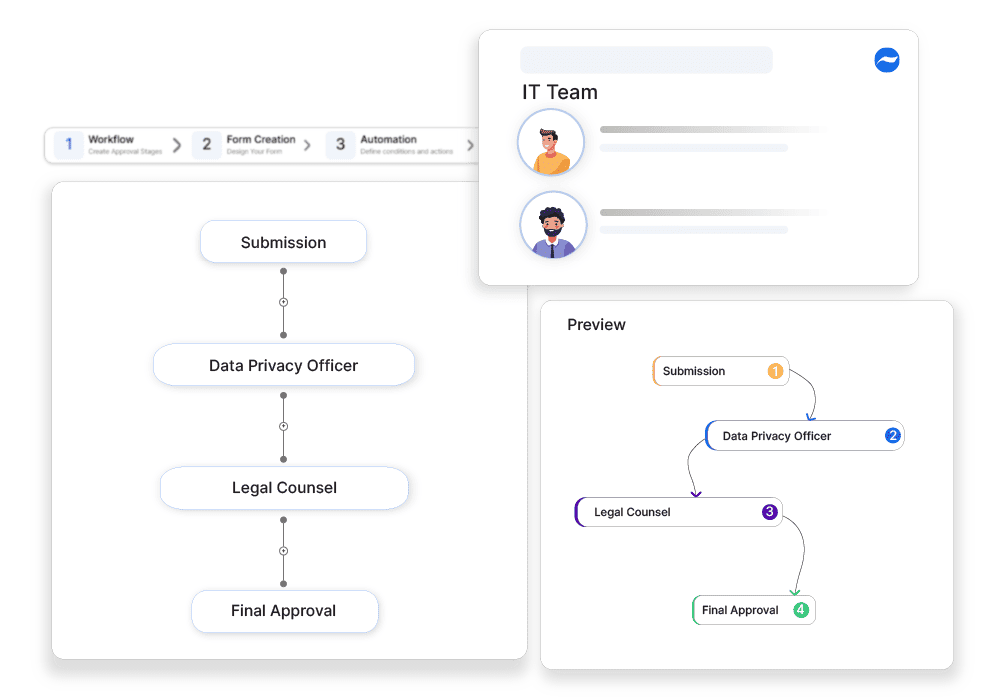
How Cflow Helps:
Approval-Based Data Access Requests
Cflow ensures that every request for sensitive data goes through an approval workflow. Approvers can review the request, verify necessity, and approve or deny access, ensuring only authorized users handle sensitive data.
Privacy Policy Enforcement
Organizations can configure custom policies within Cflow to ensure that requests meet predefined privacy criteria before approval. If a request does not align with security policies, it is automatically rejected or escalated.
Time-Limited Data Access Approvals
Cflow can enforce temporary data access, ensuring that users only retain access for a specified period before automatic revocation. This reduces long-term data exposure risks.
Full Audit Trail & Compliance Logs
Every approved request is recorded in Cflow, creating a secure audit trail for compliance verification. Organizations can generate reports to demonstrate adherence to privacy regulations.
Frequently Asked Questions
What is a data privacy compliance check?
A process to ensure that data handling practices align with privacy regulations like GDPR or CCPA.
What are the main challenges in data privacy compliance checks?
Complex regulatory requirements, lack of visibility into data flows, and inconsistent audit trails.
How can businesses streamline data privacy compliance checks?
By using data mapping tools, automating compliance monitoring, and conducting regular audits.



