Secrets Management and Access Control Workflow
Automate secrets management approvals to protect sensitive credentials and enforce security best practices.
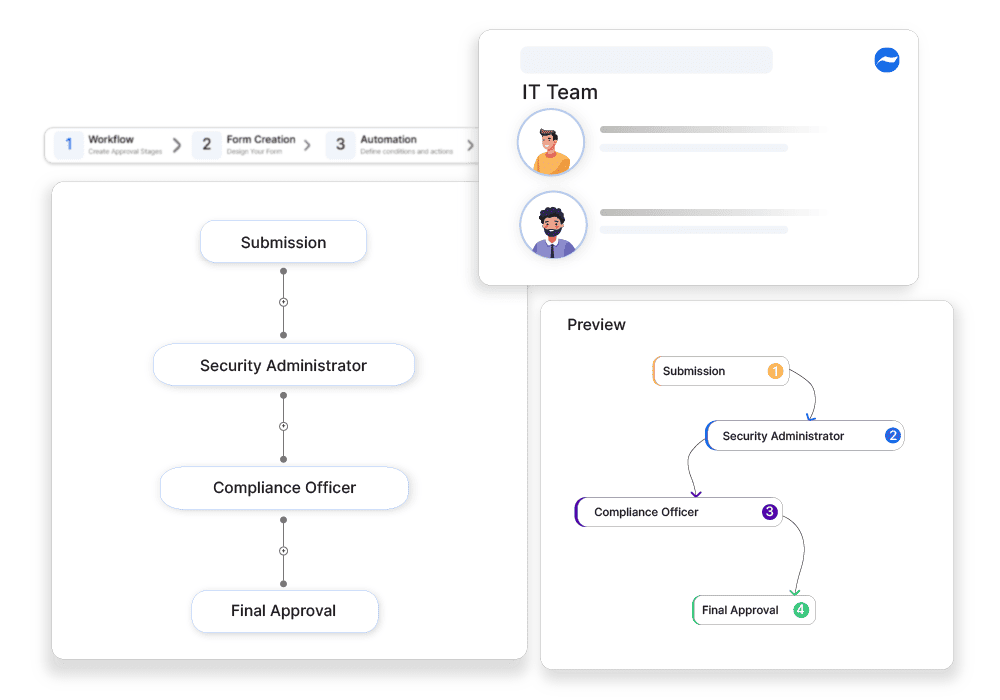
Why automate?
Secrets management involves storing, accessing, and securing API keys, passwords, and encryption keys. Without structured approvals, secrets may be exposed, mismanaged, or used improperly, leading to security breaches. Manually handling secrets access increases the risk of unauthorized exposure, making tracking and auditing access difficult. A structured approval process ensures that sensitive credentials are properly protected and only accessible to authorized users. Cflow helps to automate Secrets Management Approvals, ensuring that credential access and modifications are reviewed, approved, and logged, improving security posture.
How Cflow Helps:
Approval-Based Secrets Access
Cflow ensures that all credential access requests follow structured approvals, preventing unauthorized usage.
Compliance with Security Best Practices
Approved secret management policies align with zero-trust security frameworks, reducing exposure risks.
Role-Based Access Approvals
Only authorized personnel can approve and access sensitive credentials, improving security.
Full Audit Log for Secrets Access
Cflow logs all approved secret modifications, enabling IT teams to track access history.
Frequently Asked Questions
What is secrets management and access control?
A process to securely store and control access to credentials, API keys, and other sensitive data.
What are the main challenges?
Hardcoded secrets, excessive permissions, and secret sprawl.
How can it be improved?
By using secret management tools (like Vault) and enforcing least-privilege access.



