- Cflow
- VPN Access Authorization Automation
VPN Access Authorization Automation

Clow Team

VPN access allows remote employees, contractors, and third-party vendors to securely connect to internal networks. Without automation, manual VPN authorization leads to security breaches, policy violations, and compliance risks. Recent industry research shows that 63% of data breaches involve improperly managed remote access credentials.
Without automation, IT administrators, security teams, HR managers, compliance officers, and executives struggle to ensure appropriate access controls, policy compliance, and timely deactivation of inactive credentials. This guide walks you through exactly how Cflow automates VPN Access Authorization Process, from request submission to final IT provisioning.
What Is VPN Access Authorization Process?
The VPN Access Authorization Process governs how employees and vendors request, justify, and receive secure remote access to company systems, ensuring that proper approvals, security policies, and compliance requirements are met.
Think of VPN access as digital gatekeeping , every access request must be validated for business need, role suitability, and security impact.
Recent industry research shows that automating VPN authorizations reduces access approval time by 55% while strengthening cybersecurity posture by 60%.
Why VPN Access Authorization Matters for Organizations
Security Protection
Compliance
Role-Based Access Control
Timely Deactivation
Audit Trail
Key Benefits of Automating VPN Access Authorization with Cflow
- Centralized Access Request Portal: Cflow allows employees, contractors, or vendors to submit VPN access requests, business justifications, and manager endorsements into a controlled workflow. All request data is captured in structured formats to eliminate email back-and-forth and manual tracking.
- Dynamic Routing Based on Role & Duration: Cflow applies routing logic based on requester type (employee, contractor, vendor), data sensitivity, and requested access duration. This ensures that high-risk or long-term access requests receive additional scrutiny from appropriate teams.
- Multi-Level Review Workflows: Requests route through HR, IT security, compliance, and executive leadership depending on risk classification. Each stakeholder has defined responsibilities, reducing confusion and improving response accountability.
- Real-Time Notifications & Escalations: Automated alerts ensure timely reviews while escalations prevent delays that disrupt operations. Cflow tracks pending actions and re-routes overdue tasks to backup reviewers to avoid access bottlenecks.
- Access Duration & Auto-Expiry Controls: Cflow enforces access duration limits with automated expiry dates, renewal reminders, and mandatory periodic reviews for extended access. This reduces the risk of unauthorized long-term VPN access from inactive users or expired contracts.
- Full Audit Trail & Compliance Logs: All requests, approvals, credential provisioning, and revocations are archived for security audits and regulatory inspections. Admins can filter and retrieve records instantly during internal reviews or third-party assessments.
- Mobile Accessibility: Managers and security teams can review and approve VPN requests remotely, ensuring business continuity without delay. This flexibility supports round-the-clock access control across globally distributed teams.
Get the best value for money with Cflow
User Roles & Permissions
Requester (Employee or Contractor)
- Responsibilities: Submit VPN access request with purpose, duration, and project reference.
- Cflow Permission Level: Submit Form.
- Mapping: “Users Group.”
HR Manager
- Responsibilities: Verify employment status, contractual terms, and access eligibility.
- Cflow Permission Level: Approve/Reject.
- Mapping: “HR Team.”
IT Security Officer
- Responsibilities: Validate technical feasibility, security risks, and infrastructure readiness.
- Cflow Permission Level: Approve/Reject.
- Mapping: “IT Security Group.”
Compliance Officer
- Responsibilities: Ensure adherence to regulatory, legal, and data privacy obligations.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Compliance Group.”
Executive Sponsor (Final Approver)
- Responsibilities: Authorize high-risk or extended access requests.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Executive Board.”
Discover why teams choose Cflow
Form Design & Field Definitions
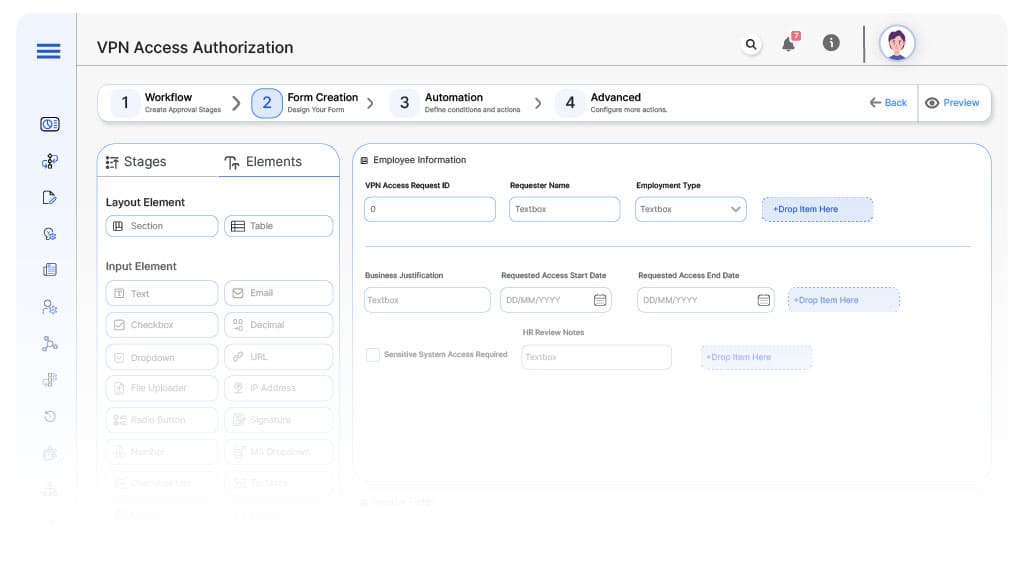
Field Label: VPN Access Request ID
- Type: Autonumber
- Auto-Populate: Generated on submission.
Field Label: Requester Name
- Type: Text (Auto-filled from user profile)
- Logic/Rules: Mandatory.
Field Label: Employment Type
- Type: Dropdown (Employee, Contractor, Vendor)
- Logic/Rules: Drives routing.
Field Label: Business Justification
- Type: Text Area
- Logic/Rules: Mandatory.
Field Label: Requested Access Start Date
- Type: Date Picker
- Logic/Rules: Mandatory.
Field Label: Requested Access End Date
- Type: Date Picker
- Logic/Rules: Enforces auto-expiry.
Field Label: Sensitive System Access Required
- Type: Checkbox (Yes/No)
- Logic/Rules: Additional review if yes.
Field Label: HR Review Notes
- Type: Text Area
- Logic/Rules: Required.
Field Label: IT Security Review Notes
- Type: Text Area
- Logic/Rules: Required
Field Label: Compliance Review Notes
- Type: Text Area
- Logic/Rules: Required
Field Label: Executive Approval Comments
- Type: Text Area
- Logic/Rules: Required
Field Label: Access Provisioning Confirmation
- Type: Checkbox
- Logic/Rules: Marks access fully provisioned.
Transform your Workflow with AI fusion
Approval Flow & Routing Logic
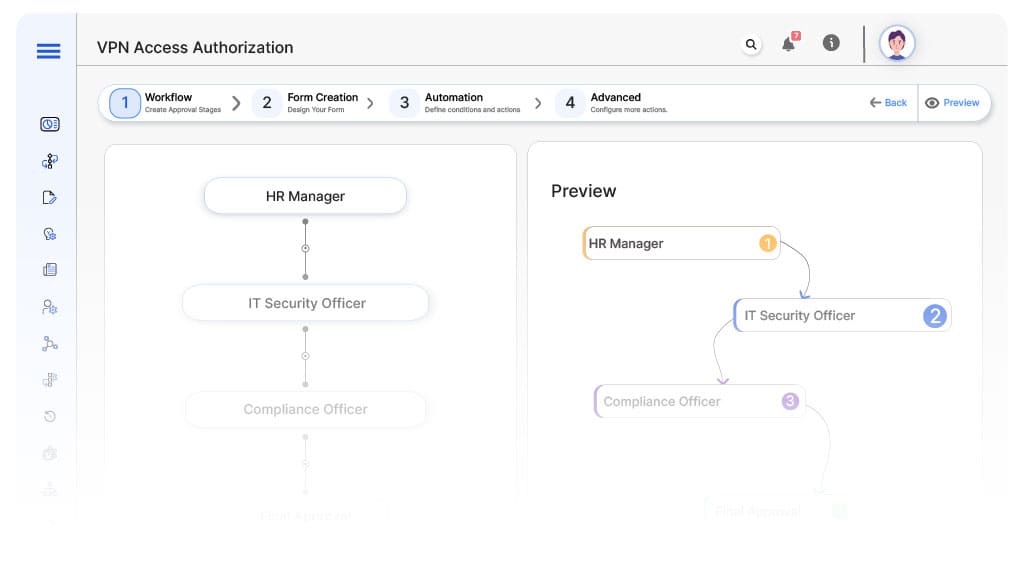
Submission → HR Manager
- Status Name: Pending HR Review
- Notification Template: “Hi HR, VPN access request requires employment eligibility review.”
- On Approve: Moves to IT Security Officer.
- On Reject: Returns to Requester.
- Escalation: Reminder after 1 day.
HR → IT Security Officer
- Status Name: Pending IT Security Review
- Notification Template: “Hi IT Security, evaluate infrastructure risks for access request.”
- On Approve: Moves to Compliance Officer.
- On Reject: Returns to HR Manager.
- Escalation: Reminder after 1 day.
IT Security → Compliance Officer
- Status Name: Pending Compliance Review
- Notification Template: “Hi Compliance, validate regulatory compliance for requested access.”
- On Approve: Moves to Executive Sponsor.
- On Reject: Returns to IT Security Officer.
- Escalation: Reminder after 1 day.
Compliance → Executive Sponsor
- Status Name: Pending Final Approval
- Notification Template: “Hi Executive, high-risk VPN request ready for final authorization.”
- On Approve: Moves to VPN Provisioned.
- On Reject: Returns to Compliance Officer.
- Escalation: Reminder after 1 day.
Final → VPN Provisioned
- Status Name: VPN Access Fully Authorized
- Notification Template: “VPN access approved. IT provisioning team may activate credentials.”
Transform your AI-powered approvals
Implementation Steps in Cflow
Create a new workflow
Design the form
Set up User Roles/Groups
Build the process flow diagram
Configure notifications
Apply templates and escalation rules per Approval Flow.
Set conditional logic
Save and publish workflow
Activate process.
Test with a sample request
Adjust logic if needed
Go live
Example Journey: New Contractor VPN Access
FAQ's
Unleash the full potential of your AI-powered Workflow

