- Cflow
- Penetration Testing Approval Automation
Penetration Testing Approval Automation

Clow Team

Penetration testing, or ethical hacking, is essential for identifying vulnerabilities in enterprise systems before malicious actors can exploit them. However, the internal approval process for launching a pentest is often slow, fragmented, and non-compliant. With increasing security risks and regulatory scrutiny, delays in pentest approval can leave critical systems exposed.
Manual approval chains across Information Security, IT Operations, Legal, and third-party vendors often result in missed SLAs, untracked communications, and audit gaps. This guide breaks down how Cflow automates the Penetration Testing Approval Process — ensuring that every step is secure, compliant, and aligned with internal security policies.
What Is Penetration Testing Approval Process?
The Penetration Testing Approval Process governs how organizations formally authorize internal or external penetration testing activities across their digital assets. It ensures stakeholder alignment, risk assessments, legal clearances, and infrastructure readiness before simulated attacks are conducted.
Think of it as a pre-flight checklist before performing high-risk, system-wide simulations. Without automation, this process becomes a bottleneck involving disjointed emails, unclear roles, and delayed security validation.
According to cybersecurity best practices, organizations that automate pentest approvals reduce pre-test delays by up to 60% and demonstrate better audit readiness under SOC 2, ISO 27001, and PCI-DSS.
Why Penetration Testing Approval Process Is Important
Risk Governance
Legal Compliance
Operational Safety
Audit Readiness
Key Benefits of Automating Penetration Testing Approval Process with Cflow
- Centralized Approval Portal: All stakeholders – InfoSec, IT, Legal, and Vendor Managers – work from a shared interface. Cflow routes tasks, tracks status, and logs approvals in real-time, removing manual coordination errors. This eliminates email threads and ensures transparency across every approval step.
- Role-Based Routing by Test Type: Cflow dynamically adjusts workflows based on pentest type (web app, infrastructure, cloud, API). Legal might be skipped for internal-only scans, while vendor NDAs are triggered for third-party tests.
- Automated Risk Categorization: Upon submission, Cflow categorizes each request based on asset type, business impact, and data sensitivity. High-risk tests trigger executive oversight automatically. This ensures proper risk mitigation strategies are applied before execution.
- Real-Time Alerts & Escalations: Stakeholders receive alerts at every stage. If Legal hasn’t signed off within 48 hours, escalations are auto-triggered to InfoSec heads or Compliance teams. Cflow ensures no critical step is overlooked or delayed.
- Policy & Documentation Enforcement: The workflow enforces uploads of NDAs, risk assessments, and test scopes. If any document is missing, the process cannot proceed, ensuring full audit compliance. This guarantees every test meets internal security and legal standards.
- Audit Logs & Approval Records: Every action – form edits, task completion, approval timestamps is logged. Cflow allows audit teams to pull penetration test approval records instantly for compliance checks. This facilitates fast response to regulatory audits and security reviews.
- Mobile & Remote Approvals: Stakeholders can review scopes, approve NDAs, or reject requests securely via mobile. This keeps testing timelines intact even with remote legal or IT teams. Approvals happen faster, regardless of time zones or location.
Get the best value for money with Cflow
User Roles & Permissions
Requestor (Security Analyst or DevSecOps)
- Responsibilities: Submit pentest request, scope, asset details, preferred vendor
- Permission: Submit Form
- Group Mapping: “Security Team”
InfoSec Reviewer
- Responsibilities: Review technical scope, align with risk tolerance
- Permission: Approve/Reject
- Group Mapping: “InfoSec Group”
IT Infrastructure Owner
- Responsibilities: Confirm asset availability, backup readiness, system monitoring
- Permission: Task Owner
- Group Mapping: “IT Operations”
Legal Reviewer
- Responsibilities: Review and approve vendor contracts, data clauses, NDAs
- Permission: Approve/Reject
- Group Mapping: “Legal Team”
Vendor Coordinator
- Responsibilities: Confirm third-party readiness, issue credentials, validate scope
- Permission: Task Owner
- Group Mapping: “Vendor Management”
Compliance Auditor
- Responsibilities: View full approval trail and documentation
- Permission: View Only
- Group Mapping: “Compliance Team”
Discover why teams choose Cflow
Form Design & Field Definitions
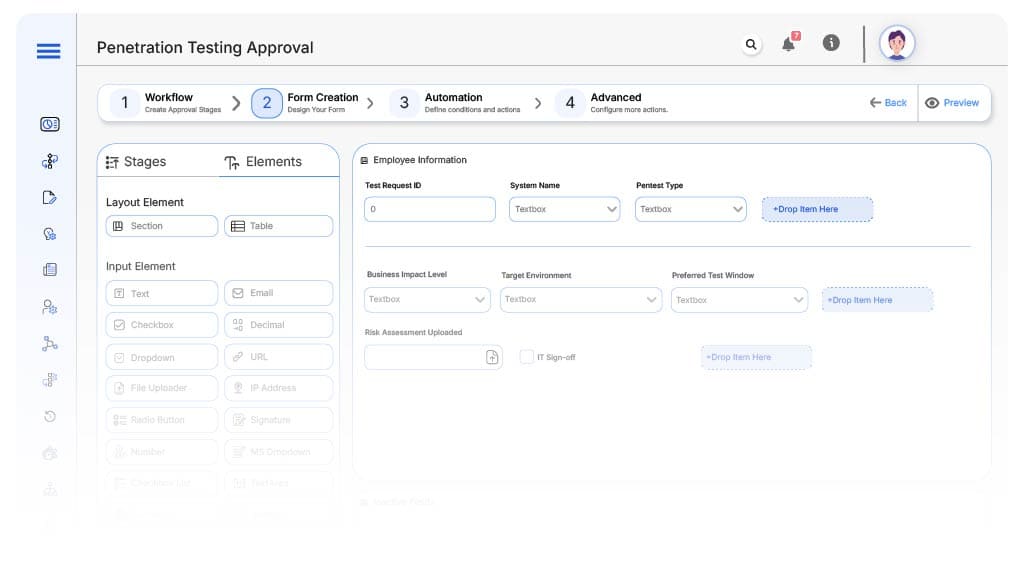
Field Label: Test Request ID
- Type: Autonumber
- Auto-Populate: on submission.
Field Label: Asset/System Name
- Type: Text
- Logic/Rules: Required.
Field Label: Pentest Type
- Type: Dropdown (Web App, Infrastructure, Cloud, API, Physical)
- Logic/Rules: Drives routing logic based on selection.
Field Label: Business Impact Level
- Type: Dropdown (Low, Medium, High)
- Logic/Rules: High-level triggers executive review step
Field Label: Target Environment
- Type: Dropdown (Production, Staging, Development)
- Logic/Rules: Determines scheduling constraints and IT coordination.
Field Label: Preferred Test Window
- Type: Date Range Picker
- Logic/Rules: Required to plan execution windows with IT.
Field Label: Third-Party Vendor Used
- Type: Dropdown
- Logic/Rules: Triggers mandatory NDA and Legal approval routing.
Field Label: Risk Assessment Uploaded
- Type: File Upload
- Logic/Rules: Mandatory upload for Medium and High Business Impact levels.
Field Label: Legal Approval Status
- Type: Checkbox
- Logic/Rules: Must be checked before proceeding with vendor testing.
Field Label: NDA Attached
- Type: File Upload
- Logic/Rules: Blocks workflow progression if missing for external vendors.
Field Label: InfoSec Comments
- Type: Text Area
- Logic/Rules: Optional; used for internal notes and justifications.
Field Label: IT Sign-off
- Type: Checkbox
- Logic/Rules: Required to confirm system readiness before test begins.
Field Label: Final Approval Confirmation
- Type: Checkbox
- Logic/Rules: Checked by InfoSec after all departments complete their tasks.
Transform your Workflow with AI fusion
Approval Flow & Routing Logic
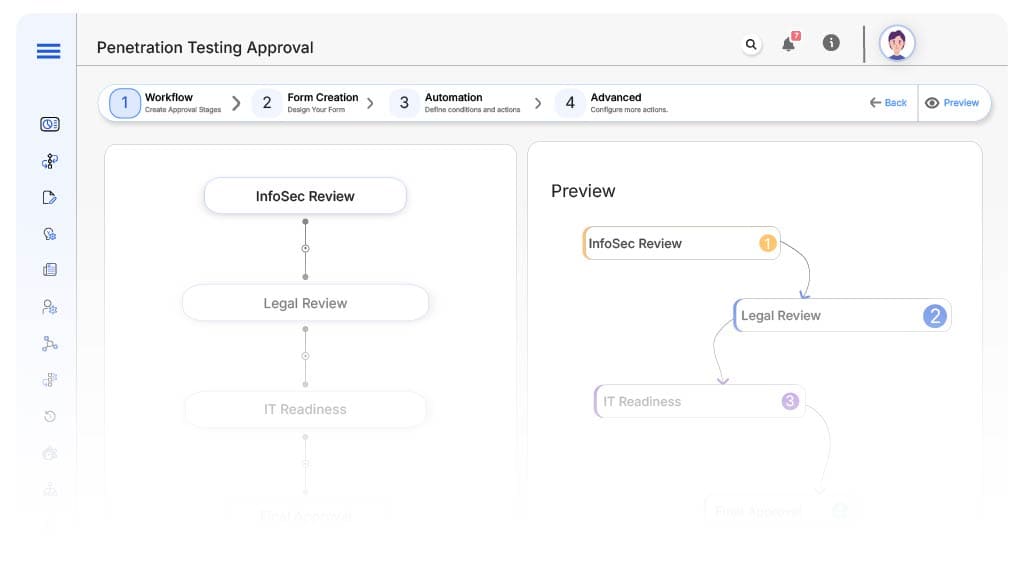
Submission → InfoSec Review
- Status: Pending InfoSec Review
- Notification: “New pentest request for {System}. Please review scope.”
- On Approve: Routes to Legal & IT simultaneously
InfoSec → Legal Review
- Status: Pending Legal Approval
- Notification: “Review NDA and vendor contracts for {System}.”
- Escalation: 48-hour reminder
InfoSec → IT Readiness
- Status: Pending IT Confirmation
- Notification: “Check if system {Asset} is ready for testing.”
- Escalation: 48-hour reminder
Legal → Vendor Coordination
- Status: Vendor Credentialing
- Notification: “Send credentials and scope to {Vendor}.”
- On Complete: Sends to InfoSec for Final Approval
IT → Final Review by InfoSec
- Status: Awaiting Final Sign-Off
- Notification: “All departments completed tasks. Please confirm launch.”
Final → Approval Complete
- Status: Approved for Execution
- Notification: “Pentest for {System} is now fully approved.”
Transform your AI-powered approvals
Implementation Steps in Cflow
Create a new workflow
Design the form
Set up User Roles/Groups
Build flow
Apply logic
Configure alerts
Activate
Test flow
Go live
Example Journey: External Pentest for CRM
FAQ's
Unleash the full potential of your AI-powered Workflow

