- Cflow
- Firewall Rule Change Automation
Firewall Rule Change Automation

Clow Team

Firewall rule changes control access to critical systems and applications. Without automation, manual firewall rule updates create security vulnerabilities, non-compliant configurations, and operational disruptions. Recent industry research shows that 47% of network breaches involve misconfigured or unauthorized firewall rule changes.
Without automation, IT security teams, network administrators, compliance officers, legal counsel, and leadership struggle to enforce change control, validate risk impact, and ensure audit readiness. This guide walks you through exactly how Cflow automates Firewall Rule Change Process, from rule change request submission to final implementation authorization.
What Is Firewall Rule Change Process?
The Firewall Rule Change Process governs how network access requests are proposed, evaluated, approved, tested, and implemented to protect corporate systems from external and internal threats.
Think of firewall rule changes as network gate modifications , every change must be validated for security, compliance, and operational impact.
Recent industry research shows that automating firewall change control reduces misconfiguration risks by 65% and improves audit compliance by 55%.
Why VPN Access Authorization Matters for Organizations
Cybersecurity Protection
Compliance
Ensures adherence to data protection, privacy, and cybersecurity regulations.
Role-Based Access Control
Change Control
Operational Stability
Audit Trail
Key Benefits of Automating Firewall Rule Change Process with Cflow
- Centralized Rule Change Request Portal: Cflow allows network engineers or requestors to submit firewall rule change requests, justification, affected systems, and risk assessments into a structured workflow.This eliminates fragmented email chains and undocumented manual interventions in firewall management.
- Dynamic Routing Based on Risk Level: Cflow applies routing logic based on requested change severity, system sensitivity, and external exposure. Low-risk internal changes route to network ops, while high-risk public-facing changes go to executive security. Risk-based routing reduces approval bottlenecks while ensuring critical changes are fully vetted.
- Multi-Level Review Workflows: Requests route through IT security, network operations, compliance, legal, and executive leadership depending on risk classification. Each stakeholder signs off based on their domain – technical, legal, or compliance risk. This layered review prevents risky changes from slipping through without scrutiny.
Real-Time Notifications & Escalations: Automated alerts ensure timely risk assessments while escalation rules prevent unreviewed changes. Notifications are triggered for pending approvals, stalled reviews, or incomplete documentation. Escalation paths route overdue tasks to higher-level reviewers or backup approvers. - Pre-Change Testing & Validation Controls: Cflow enforces test validations, rollback plan documentation, and rollback responsibility assignments before changes go live. Change implementers must confirm sandbox testing and attach validation screenshots or logs. Rollback plans are mandatory, with designated owners and clear activation triggers.
Full Audit Trail & Compliance Logs: All firewall change requests, impact assessments, approvals, and rollback events are archived for security audits and compliance certifications. Every action—submission, review, update, or rollback—is timestamped and traceable. Audit logs can be exported or queried based on IPs, users, or rule types. Cflow supports compliance standards like ISO 27001, NIST, and internal audit frameworks.
Get the best value for money with Cflow
User Roles & Permissions
Requester (Network Engineer or Application Owner)
- Responsibilities: Submit firewall rule change request with affected IPs, ports, and justification.
- Cflow Permission Level: Submit Form.
- Mapping: “Network Change Requestors.”
IT Security Analyst
- Responsibilities: Evaluate security implications, external threats, and compliance exposure.
- Cflow Permission Level: Approve/Reject.
- Mapping: “IT Security Group.”
Network Operations Manager
- Responsibilities: Validate feasibility, network load impact, and conflict with existing rules.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Network Operations Team.”
Compliance Officer
- Responsibilities: Ensure regulatory compliance and verify documentation completeness.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Compliance Group.”
Executive Sponsor (Final Approver)
- Responsibilities: Authorize high-risk or cross-border firewall rule changes.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Executive Board.”
Discover why teams choose Cflow
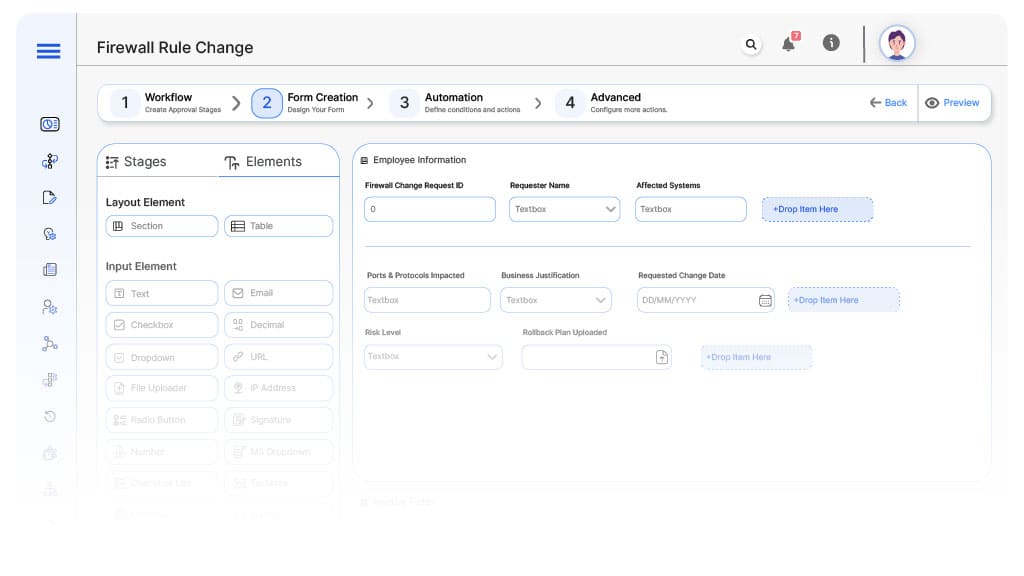
Form Design & Field Definitions
Field Label: Firewall Change Request ID
- Type: Autonumber
- Auto-Populate: Generated on submission.
Field Label: Requester Name
- Type: Text (Auto-filled from user profile)
- Logic/Rules: Mandatory.
Field Label: Affected Systems
- Type: Text Area
- Logic/Rules: Mandatory.
Field Label: Ports & Protocols Impacted
- Type: Text Area
- Logic/Rules: Mandatory.
Field Label: Business Justification
- Type: Text Area
- Logic/Rules: Mandatory.
Field Label: Requested Change Date
- Type: Date Picker
- Logic/Rules: Mandatory.
Field Label: Risk Level
- Type: Dropdown (Low, Medium, High, Critical)
- Logic/Rules: Drives routing.
Field Label: Rollback Plan Uploaded
- Type: File Upload
- Logic/Rules: Mandatory for high/critical risk levels.
Field Label: IT Security Review Notes
- Type: Text Area
- Logic/Rules: Required
Field Label: Network Operations Review Notes
- Type: Text Area
- Logic/Rules: Required
Field Label: Compliance Review Notes
- Type: Text Area
- Logic/Rules: Required
Field Label: Executive Approval Comments
- Type: Text Area
- Logic/Rules: Required.
Field Label: Change Implemented Confirmation
- Type: Checkbox
- Logic/Rules: Marks rule implemented.
Transform your Workflow with AI fusion
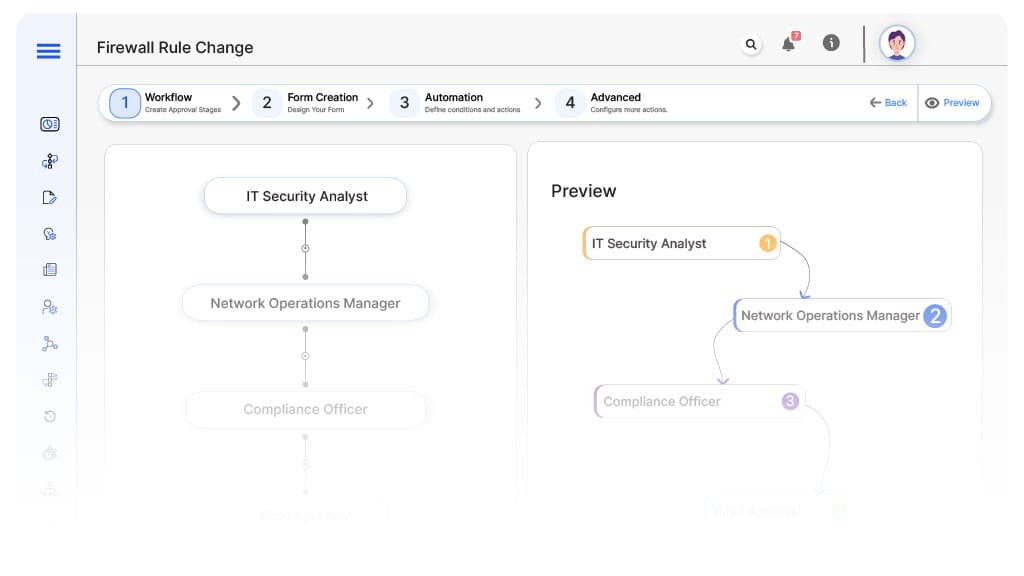
Approval Flow & Routing Logic
Submission → IT Security Analyst
- Status Name: Pending Security Review
- Notification Template: “Hi Security, firewall rule change request submitted for risk evaluation.”
- On Approve: Moves to Network Operations.
- On Reject: Returns to Requester.
- Escalation: Reminder after 1 day.
IT Security → Network Operations Manager
- Status Name: Pending Network Review
- Notification Template: “Hi Network Operations, validate technical feasibility for requested change.”
- On Approve: Moves to Compliance Officer.
- On Reject: Returns to IT Security Analyst.
- Escalation: Reminder after 1 day.
Network Operations → Compliance Officer
- Status Name: Pending Compliance Review
- Notification Template: “Hi Compliance, review documentation completeness for change control.”
- On Approve: Moves to Executive Sponsor.
- On Reject: Returns to Network Operations Manager.
- Escalation: Reminder after 1 day.
Compliance → Executive Sponsor
- Status Name: Pending Final Approval
- Notification Template: “Hi Executive, firewall rule change requires final authorization.”
- On Approve: Moves to Change Implemented.
- On Reject: Returns to Compliance Officer.
- Escalation: Reminder after 1 day.
Final → Change Implemented
- Status Name: Firewall Change Fully Authorized
- Notification Template: “Firewall rule change authorized. Network team may proceed with implementation.”
Transform your AI-powered approvals
Implementation Steps in Cflow
Create a new workflow
Design the form
Set up User Roles/Groups
Build the process flow diagram
Configure notifications
Apply templates and escalation rules per Approval Flow.
Set conditional logic
Save and publish workflow
Activate process.
Test with a sample request
Adjust logic if needed
Go live
Example Journey: External API Integration Firewall Rule
FAQ's
Setup typically completes within 3–5 business days.
Unleash the full potential of your AI-powered Workflow

