- Cflow
- Database Access Permission Automation
Database Access Permission Automation

Clow Team

Managing database access requests manually is risky, time-consuming, and error-prone. Whether it’s for onboarding new employees, temporary access for contractors, or role changes, approving access without the right checks creates security vulnerabilities and compliance risks.
Uncontrolled or delayed access can impact productivity, violate audit protocols, or expose sensitive business data. With Cflow, organizations can automate the end-to-end process of database permission requests, ensuring security, compliance, and fast provisioning.
What Is Database Access Permission Automation?
Database Access Permission Automation is a structured workflow that handles how employees request, review, approve, and receive access to enterprise databases. It routes the request through mandatory IT, InfoSec, and Manager approvals, applies conditional access logic, and ensures audit readiness.
Consider it a digital gatekeeper that ensures only authorized personnel gain access to critical data systems, with clear logging and compliance rules enforced automatically.
Automated access control significantly reduces provisioning time, enhances compliance, and removes human errors from the approval chain.
Why Database Access Permission Automation Matters
Data Security
Audit Compliance
Faster Provisioning
Role-Based Control
Revocation Workflow
Key Benefits of Automating Database Access Permissions with Cflow
- Centralized Access Request System: All database access requests are submitted and tracked in a single Cflow dashboard. IT, InfoSec, and Managers can view, approve, or reject with full visibility. This unified approach avoids scattered emails and simplifies access governance. Teams can quickly identify bottlenecks and pending actions from a central interface.
- Role-Based Access Controls: Permission logic is configured by role, department, and project need. For example, a developer may only request access to test databases, not production. Access is always aligned with job responsibilities and data sensitivity. Prevents unauthorized access by ensuring only qualified users see relevant data.
- Compliance & Audit Trail: Every request is logged with timestamped approvals and comments. Cflow makes it easy to export access logs for audits or internal reviews. This supports IT audit readiness and strengthens internal compliance. Regulatory teams can demonstrate complete access transparency when required.
- Conditional Approval Routing: High-risk or production database access routes through additional InfoSec approval, while read-only requests may follow a lighter flow. This ensures higher scrutiny for sensitive environments without slowing down lower-risk requests. The logic can be easily customized to meet internal policy requirements.
- Automated Notifications & Expirations: Cflow sends reminders for pending approvals, notifies when access is granted, and even schedules automatic access revocation based on expiry dates. Time-bound access minimizes long-term exposure and reduces manual tracking. This eliminates forgotten access, lowering potential security risks.
- Secure Document Uploads: Users can attach supporting documents like manager endorsements or training certificates. Cflow validates uploads before routing. This ensures only complete and verified requests are processed. Sensitive files are stored securely and encrypted during workflow handling.
- Mobile-Ready Approval: IT managers and security teams can approve access requests from mobile devices, ensuring no delays in provisioning. Approvers stay responsive even when away from their desks. This accelerates approvals during travel, weekends, or urgent access needs.
Get the best value for money with Cflow
User Roles & Permissions
Employee (Requestor)
- Responsibilities: Submit request for database access.
- Cflow Permission Level: Submit Form.
- Mapping: “Employees” group.
Reporting Manager
- Responsibilities: Validate the business need for access.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Managers” group.
IT Admin
- Responsibilities: Provision access credentials, validate access logs.
- Cflow Permission Level: Task Owner.
- Mapping: “IT Team” group.
InfoSec Reviewer
- Responsibilities: Approve or deny high-risk access; enforce compliance.
- Cflow Permission Level: Approve/Reject.
- Mapping: “InfoSec” group.
Database Owner
- Responsibilities: Final validation for critical database access.
- Cflow Permission Level: Approve/Reject.
- Mapping: “DB Admin” group.
Audit Viewer
- Responsibilities: Review archived access logs for audits.
- Cflow Permission Level: View Only.
- Mapping: “Audit” group.
Discover why teams choose Cflow
Form Design & Field Definitions
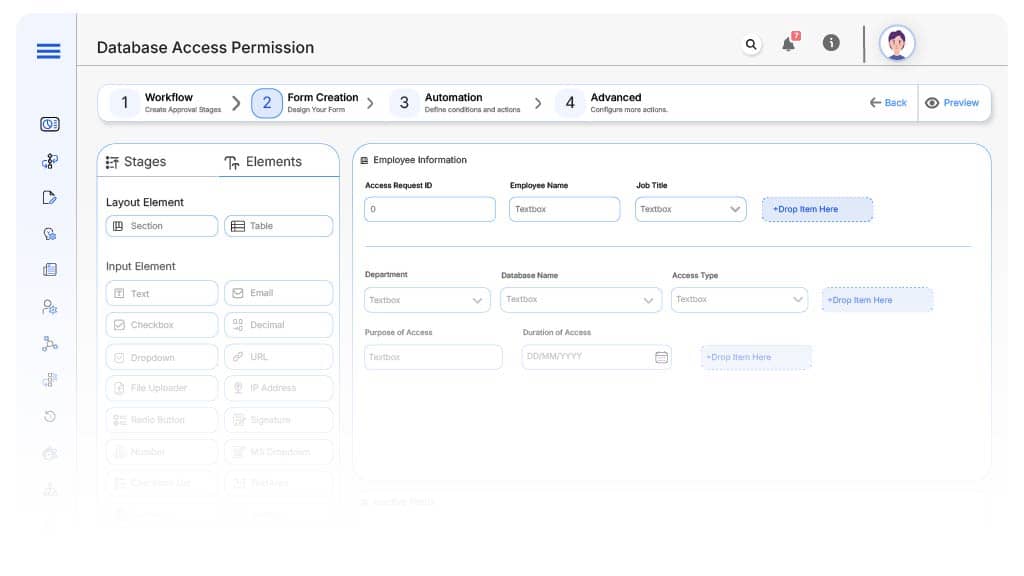
Field Label: Access Request ID
- Type: Autonumber
- Auto-Populate: Generated on submission.
Field Label: Employee Name
- Type: Text (Read-only)
- Auto-Populate: From HRMS
Field Label: Job Title
- Type: Dropdown
- Auto-Populate: From user profile
Field Label: Department
- Type: Dropdown
- Auto-Populate: From HRMS
Field Label: Database Name
- Type: Dropdown (List of DBs: Oracle, SQL, Mongo, etc.)
- Logic/Rules: Required
Field Label: Access Type
- Type: Dropdown (Read, Write, Admin)
- Logic/Rules: Triggers routing logic
Field Label: Purpose of Access
- Type: Text Area
- Logic/Rules: Mandatory for Manager Review
Field Label: Duration of Access
- Type: Date Range
- Logic/Rules: Required; drives auto-expiration
Field Label: Manager Approval
- Type: Checkbox
- Logic/Rules: Must be approved to proceed
Field Label: InfoSec Review Needed
- Type: Conditional Checkbox
- Logic/Rules: Required for write/admin access
Field Label: Supporting Documents
- Type: File Upload
- Logic/Rules: Optional but validated if uploaded
Field Label: Final Access Approval
- Type: Checkbox
- Logic/Rules: Required before provisioning
Field Label: IT Provisioning Completed
- Type: Checkbox
- Logic/Rules: Checked by IT after access setup
Field Label: Access Expiry Set
- Type: Date Picker
- Logic/Rules: Sets expiry reminder
Transform your Workflow with AI fusion
Approval Flow & Routing Logic
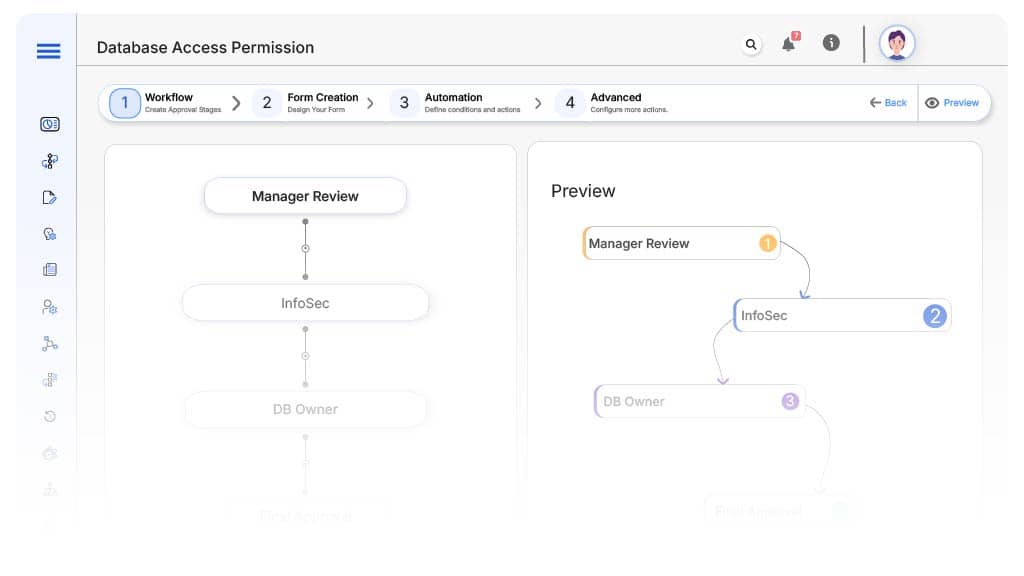
Submission → Manager Review
- Status Name: Pending Manager Approval
- Notification: “Hi {Manager}, please review {Employee}’s access request.”
- On Approve: Routes to InfoSec if required, else to IT.
Manager → InfoSec (Conditional)
- Status Name: Pending InfoSec Review
- Notification: “InfoSec: Review high-privilege access request from {Employee}.”
- Escalation: Reminder in 2 days
- On Approve: Routes to DB Owner
InfoSec → DB Owner
- Status Name: Pending Database Owner Approval
- Notification: “Please validate access request to {Database} by {Employee}.”
- On Approve: Routes to IT
IT Admin → Provisioning
- Status Name: Pending Finance Review
- Notification Template: “Hi Finance, subscription cost and budget impact require review.”
- On Approve: Moves to CIO / Legal Counsel (if applicable).
- On Reject: Returns to Procurement Officer.
- Escalation: Reminder after 1 day.
Final → Confirmation
- Status Name: Access Granted
- Notification: “Your database access request has been approved and provisioned.”
- Action: Archive for audit
Transform your AI-powered approvals
Implementation Steps in Cflow
Create a new workflow
Design the form
Set up User Roles/Groups
Build the process flow diagram
Configure notifications
Set conditional logic
Save and publish workflow
Test with a sample request
Adjust logic if needed
Go live
Example Journey: Priya's Request
FAQ's
Cflow includes expiry date fields and automated triggers that notify IT or revoke access when the duration lapses.
Unleash the full potential of your AI-powered Workflow

