- Cflow
- Data Encryption Policy Update Automation
Data Encryption Policy Update Automation

Clow Team

Data encryption policies must evolve rapidly to meet regulatory requirements, cybersecurity threats, and vendor compliance standards. Yet, manually updating and reviewing these policies creates silos, delays, and audit gaps. A recent IBM report shows that 45% of companies lack a consistent review process for critical IT security policies.
Without automation, IT, legal, and compliance teams often rely on disconnected emails and static documents to track policy changes, sign-offs, and implementation. This guide explains how Cflow automates the Data Encryption Policy Update process, from initiation and review to approval and publishing, ensuring visibility, accountability, and control.
What Is Data Encryption Policy Update Automation?
Data Encryption Policy Update Automation is the structured workflow that governs how encryption policies are reviewed, updated, approved, and circulated within an organization. It replaces manual tracking with automated reminders, role-based approvals, and audit logs.
This ensures that encryption standards whether for endpoints, servers, or cloud environments are always current, compliant, and formally documented.
Research shows that organizations with automated policy governance reduce IT audit failures by 40% and increase implementation accuracy by 60%.
Why Data Encryption Policy Update Automation Matters for Organizations
Faster Policy Revisions
Compliance Alignment
Controlled Review Process
Cross-Team Visibility
Audit-Ready Records
Key Benefits of Automating Data Encryption Policy Updates with Cflow
- Trigger-Based Policy Update Initiation: Cflow auto-triggers workflows based on revision cycles, regulation changes, or internal audits. Teams are instantly notified to begin the review process. This eliminates delays and ensures encryption standards stay current.
- Structured Multi-Department Review: Policies move through IT, compliance, legal, and executive review stages with predefined tasks. Each department reviews the document based on their area of responsibility. This ensures balanced evaluation and collective ownership.
- Clause Validation & Version Control: Policy changes are checked for alignment with existing security frameworks. Cflow tracks version history and provides side-by-side comparisons. This ensures transparency and prevents unauthorized or duplicate changes.
- Escalation & SLA Alerts: If a reviewer delays action, Cflow escalates the task with reminders and alternate routing. SLA-based timing ensures the policy update cycle stays on track. This prevents security delays or compliance violations.
- Secure Document Attachments & Approval Trails: All supporting documentation, change notes, and approvals are stored securely within Cflow. Time-stamped logs provide traceability for every action. This creates a complete audit trail for security teams and regulators.
- Mobile Access for Leadership Review: Executives can review, comment, and approve encryption policy changes from their mobile devices. Approvals don’t get delayed due to travel or limited availability. This accelerates adoption and business continuity.
Get the best value for money with Cflow
User Roles & Permissions
IT Security Analyst (Initiator)
- Responsibilities: Submit updated encryption policy drafts based on technical requirements.
- Cflow Permission Level: Submit Form
- Mapping: “IT Security Team”
Compliance Officer
- Responsibilities: Review updated policies for compliance with internal standards and external regulations.
- Cflow Permission Level: Approve/Reject
- Mapping: “Compliance Team”
Legal Counsel
- Responsibilities: Ensure legal soundness of encryption-related language and clauses.
- Cflow Permission Level: Approve/Reject
- Mapping: “Legal Department”
CIO / CISO (Final Approver)
- Responsibilities: Provide executive sign-off before publishing and enforcing the updated policy.
- Cflow Permission Level: Approve/Reject
- Mapping: “Executive Leadership”
Discover why teams choose Cflow
Form Design & Field Definitions
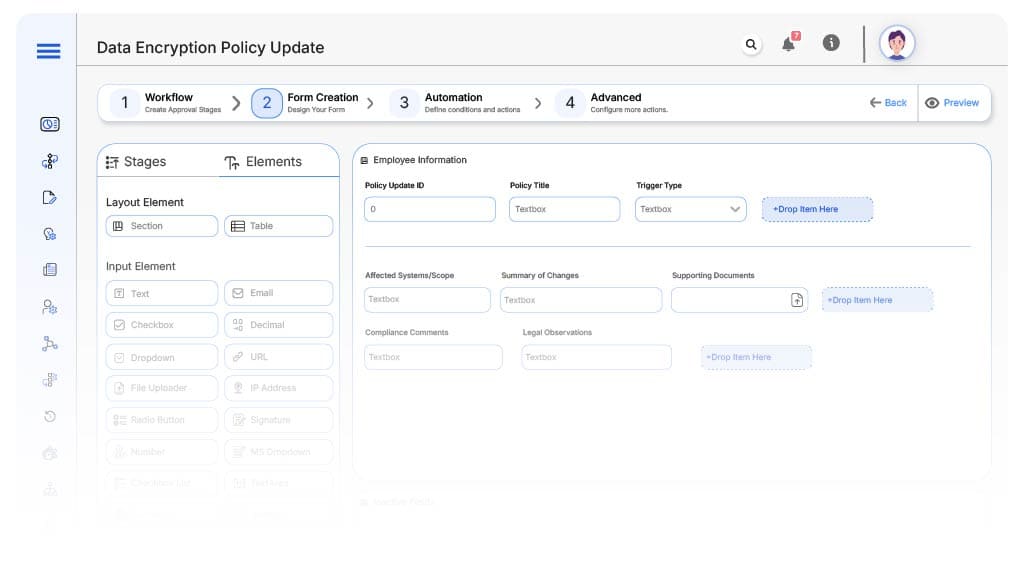
Field Label: Policy Update ID
- Type: Autonumber
- Auto-Populate: Generated on submission.
Field Label: Policy Title
- Type: Text
- Logic/Rules: Mandatory
Field Label: Trigger Type
- Type: Dropdown (Scheduled Review, Audit Finding, Regulatory Change, Security Incident)
- Logic/Rules: Drives routing
Field Label: Affected Systems/Scope
- Type: Text Area
- Logic/Rules: Required
Field Label: Summary of Changes
- Type: Text Area
- Logic/Rules: Required
Field Label: Supporting Documents
- Type: File Upload
- Logic/Rules: Mandatory
Field Label: Compliance Comments
- Type: Text Area
- Logic/Rules: Required
Field Label: Legal Observations
- Type: Text Area
- Logic/Rules: Required if legal terms updated
Field Label: Executive Sign-Off
- Type: Checkbox
- Logic/Rules: Marks final approval
Transform your Workflow with AI fusion
Approval Flow & Routing Logic
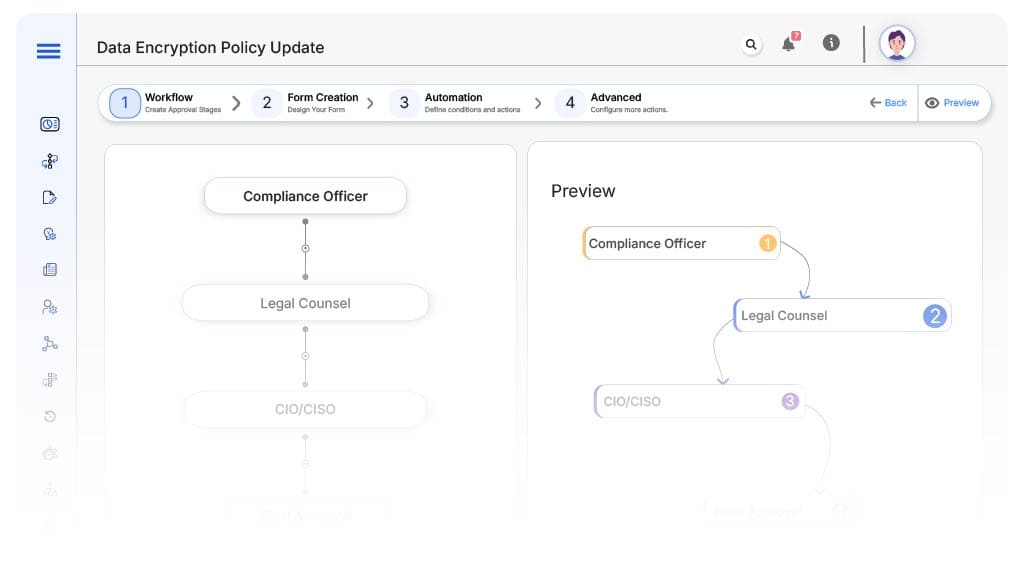
Submission → Compliance Officer
- Status Name: Pending Compliance Review
- Notification Template: “Encryption policy update submitted. Please validate changes against compliance framework.”
- On Approve: Moves to Legal
- On Reject: Returns to IT Analyst
- Escalation: Reminder after 1 day
Compliance → Legal Counsel
- Status Name: Pending Legal Review
- Notification Template: “Please review updated policy terms for legal and regulatory soundness.”
- On Approve: Moves to Executive
- On Reject: Returns to Compliance
- Escalation: Reminder after 1 day
Legal → CIO/CISO
- Status Name: Pending Executive Sign-Off
- Notification Template: “Policy ready for executive endorsement and organization-wide release.”
- On Approve: Moves to Published
- On Reject: Returns to Legal
- Escalation: Reminder after 1 day
Final → Published
- Status Name: Policy Approved & Released
- Notification Template: “Encryption policy update finalized. Begin implementation and communication rollout.”
Transform your AI-powered approvals
Implementation Steps in Cflow
Create a new workflow
Design the form
Assign roles
Build approval flow
Set escalation rules
Integrate with DMS / Security Portals
Test scenarios
Go live
Example Journey: Policy Update Execution
FAQ's
Unleash the full potential of your AI-powered Workflow

