- Cflow
- Cybersecurity Tool Investment Automation
Cybersecurity Tool Investment Automation

Clow Team

Investing in cybersecurity tools is vital to safeguarding organizational data, infrastructure, and digital operations. Manual investment approvals lead to delays, insufficient vetting, and missed compliance checks. Research shows that 53% of organizations report inefficiencies in approving security tool investments.
Without automation, IT and finance teams face difficulties validating technical needs, aligning budgets, and documenting approvals. This guide walks you through exactly how Cflow automates Cybersecurity Tool Investment Process, from request submission to executive approval.
What Is Cybersecurity Tool Investment Process?
The Cybersecurity Tool Investment Process manages how organizations assess, approve, and implement new security tools. It involves collecting business needs, evaluating risk mitigation, validating costs, and routing for multi-departmental sign-off.
This process ensures every purchase aligns with IT strategy, security posture, and budget controls. Automation enhances traceability, accelerates turnaround time, and improves investment justification. Studies show automated security procurement workflows improve review times by 45% and audit accuracy by 38%.
Why Cybersecurity Tool Investment Automation Matters for Organizations?
Risk Management
Budget Compliance
IT Strategy Alignment
Faster Decision-Making
Key Benefits of Automating Cybersecurity Tool Investment with Cflow
- Centralized Investment Request Portal: Cflow provides a unified portal where security teams can submit detailed investment requests. The form captures tool type, risk category, estimated cost, and strategic justification, enabling better tracking, prioritization, and visibility into budget cycles. This centralization prevents lost emails, inconsistent data capture, and submission delays.
- Dynamic Risk-Based Routing: Requests in Cflow are routed dynamically based on the severity of security threats, department, and investment value. A high-risk category tool like endpoint protection will automatically involve compliance and executive stakeholders. This eliminates one-size-fits-all approvals and ensures faster routing for low-risk, low-cost tools.
- Cross-Functional Review & Approval: Cflow ensures every request undergoes structured reviews by procurement, finance, compliance, and executive teams. Each team evaluates the investment from its lens – budget, regulation, policy, and strategic alignment. Stakeholders can review supporting documents, comments, and risks before approval, ensuring shared responsibility and governance.
- Built-in Vendor Comparison & Documentation: The investment form allows upload of competitive vendor quotes, security assessments, and past usage data. Teams can compare price, performance, and prior incidents. This streamlines evaluation and compliance checks while enabling transparent decision-making.
- Automated Notifications & Escalations: Cflow sends real-time alerts at every stage – submission, pending review, rejection, or approval. If any reviewer delays action, the system escalates the request to the next level automatically. Dashboards show pending tasks and bottlenecks, helping avoid investment slowdowns.
- Full Audit Trail for Security Governance: Each action from request initiation to final approval is timestamped with user ID and comments. This creates a robust audit trail for internal reviews or external security audits. Cflow’s immutable logs help organizations prove accountability, policy enforcement, and proper segregation of duties.
- ERP & Asset Tool Integration: Cflow integrates with procurement systems, finance ERPs, and IT asset management tools. Approved requests automatically trigger vendor creation, purchase order generation, or asset tracking. Integration reduces manual data entry and synchronizes cybersecurity investment flows across systems.
Get the best value for money with Cflow
User Roles & Permissions
Security Analyst (Initiator)
- Responsibilities: Initiates request outlining security gap and proposed solution.
- Cflow Permission Level: Submit Form.
- Mapping: “IT Security Team.”
Procurement Officer
- Responsibilities: Reviews vendor credibility and procurement rules.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Procurement Group.”
Finance Approver
- Responsibilities: Validates investment against allocated IT security budget.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Finance Team.”
Compliance Officer
- Responsibilities: Ensures tool meets regulatory and internal control requirements.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Compliance Group.”
CIO or CISO (Final Approver)
- Responsibilities: Grants final go-ahead after reviewing strategic alignment.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Executive Team.”
Discover why teams choose Cflow
Form Design & Field Definitions
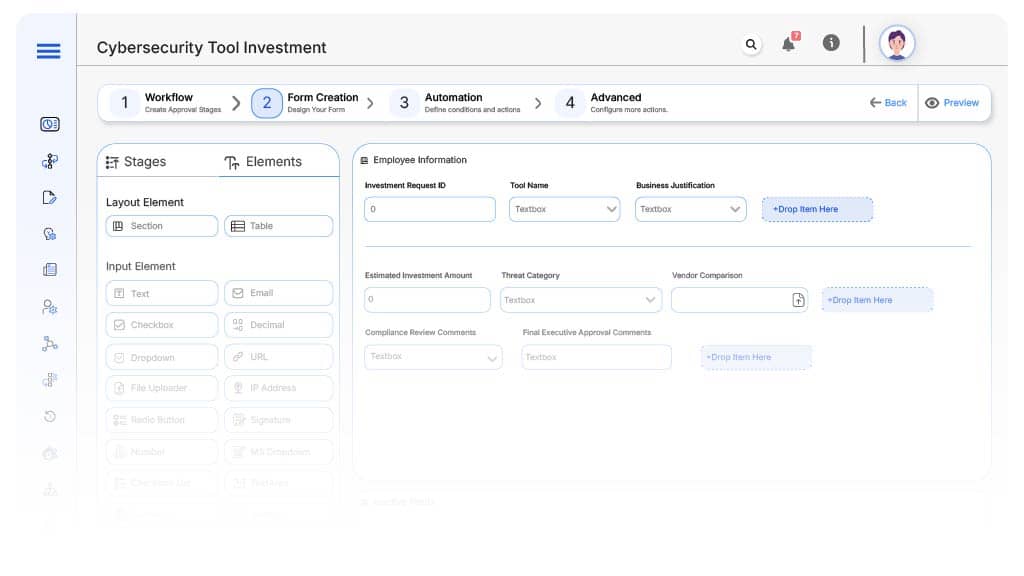
Field Label: Investment Request ID
- Type: Autonumber
- Auto-Populate: Generated on submission.
Field Label: Tool Name / Vendor
- Type: Dropdown
- Logic/Rules: Required and linked to vendor master.
Field Label: Business Justification
- Type: Text Area
- Logic/Rules: Mandatory field.
Field Label: Estimated Investment Amount
- Type: Currency Field
- Logic/Rules: Drives routing and approval levels.
Field Label: Threat Category
- Type: Dropdown (Endpoint, Network, Cloud, AppSec, GRC)
- Logic/Rules: Influences compliance involvement.
Field Label: Vendor Comparison / Attachments
- Type: File Upload
- Logic/Rules: Mandatory for new vendors.
Field Label: Compliance Review Comments
- Type: Text Area
- Logic/Rules: Required at compliance stage.
Field Label: Final Executive Approval Comments
- Type: Text Area
- Logic/Rules: Required before closing.
Transform your Workflow with AI fusion
Approval Flow & Routing Logic
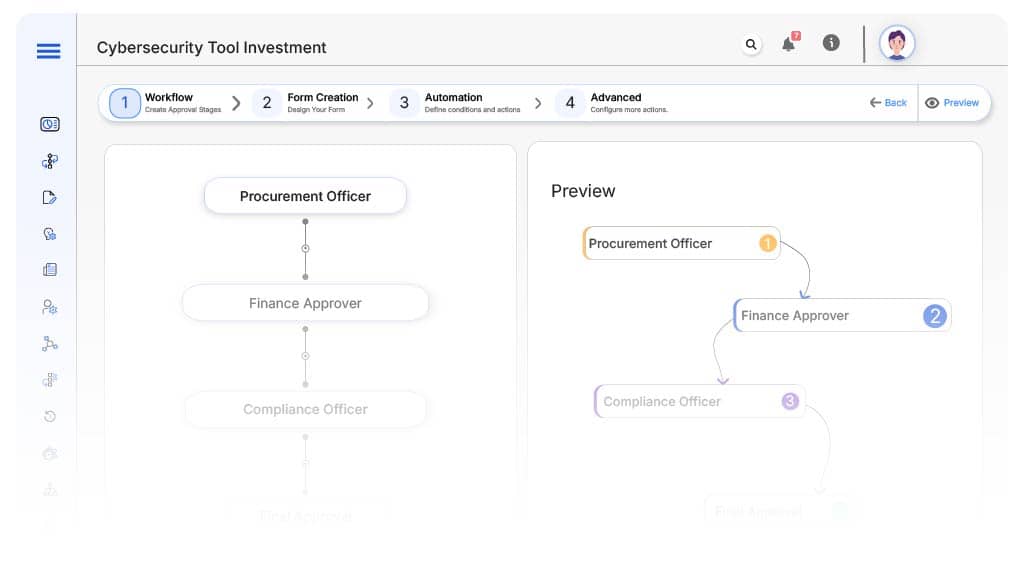
Submission → Procurement Officer
- Status Name: Pending Procurement Review
- Notification Template: “Security tool request submitted. Review vendor and sourcing validity.”
- On Approve: Route to Finance.
- On Reject: Return to Initiator.
- Escalation: Notify Procurement Head in 1 day.
Procurement Officer → Finance Approver
- Status Name: Pending Budget Review
- Notification Template: “Review budget alignment for proposed investment.”
- On Approve: Route to Compliance.
- On Reject: Return to Procurement.
- Escalation: Notify Finance Lead.
Finance Approver → Compliance Officer
- Status Name: Pending Compliance Review
- Notification Template: “Validate security tool against control standards.”
- On Approve: Route to CIO/CISO.
- On Reject: Return to Finance.
- Escalation: Notify Compliance Manager.
Compliance Officer → CIO/CISO
- Status Name: Pending Final Approval
- Notification Template: “Final executive review needed for security investment.”
- On Approve: Mark as Approved.
- On Reject: Return to Compliance.
- Escalation: Escalate to CEO Office.
Final → Security Investment Endorsed
- Status Name: Investment Fully Approved
- Notification Template: “Security tool investment fully approved. Ready for procurement and system onboarding.”
Transform your AI-powered approvals
Implementation Steps in Cflow
Create a new workflow
Go to Cflow → Workflows → New → Name “Cybersecurity Tool Investment Automation.”
Design the form
Define user groups
Design process
Add notifications
Apply logic rules
Save and test
Tweak as needed
Go live
Example Journey: Cloud Infrastructure Budget Q2
Security Analyst submits a request for $28,000 for CrowdStrike EDR. ID CST-2025-078 is generated. Procurement verifies sourcing, Finance confirms budget, Compliance checks audit controls, CIO gives final sign-off. Asset record updated and vendor onboarded.
FAQ's
Unleash the full potential of your AI-powered Workflow

