- Cflow
- Data Backup Policy Change Automation
Data Backup Policy Change Automation

Clow Team

The Data Backup Policy governs how critical data is stored, retained, and restored across an organization. Any change to this policy – such as backup frequency, storage location, or retention timelines- requires strict approvals due to security and compliance implications. Without automation, updates to backup policies are often delayed, undocumented, or miscommunicated, creating risks of non-compliance or data loss.
Manually coordinating approvals from IT, Security, Compliance, and Legal teams slows down critical updates. Tasks like documenting the change, reviewing regulatory alignment, assessing risk impact, and communicating across teams become error-prone and inconsistent. This guide shows how Cflow automates every step of Data Backup Policy Change—from initiation to audit-ready closure.
What Is Data Backup Policy Change Automation?
Data Backup Policy Change Automation is a workflow that manages how changes to backup rules, retention periods, cloud storage usage, or encryption standards are proposed, reviewed, approved, and implemented. The workflow ensures full visibility and governance over all policy alterations.
For example, if an IT admin wants to reduce backup frequency for low-priority systems, the request would need risk analysis, compliance validation, and executive approval. Cflow automates this with a structured multi-role approval system.
According to industry studies, automating IT policy changes can reduce update cycle times by 50% and eliminate undocumented changes that increase compliance risks.
Why Automate Data Backup Policy Change?
Regulatory Compliance
Faster Implementation
Clear Ownership
Audit-Ready Logs
Key Benefits of Automating Backup Policy Change with Cflow
- Centralized Policy Change Dashboard: Cflow provides a unified view of all data backup policy change requests. IT and compliance teams can track who initiated the change, what the request entails, current approval status, and final implementation notes. This replaces scattered emails and disconnected tools with a centralized, real-time source of truth.
- Role-Based Routing Logic: Policy changes are automatically routed to different teams depending on the type of change. For instance, encryption changes route to the Security team, while storage vendor changes involve Procurement. Cflow ensures the right stakeholders are included based on conditional rules without manual coordination.
- Integrated Risk Assessment Review: Cflow allows integration of risk assessment tasks within the workflow. If a change is deemed medium- or high-risk, additional review steps – such as from Legal or the CISO – are auto-triggered. This enforces structured risk handling and escalates issues early.
- Real-Time Notifications & Escalations: Automated alerts notify approvers and contributors when their input is needed. If a policy change is stuck in review beyond a configured SLA, Cflow escalates to department heads or compliance leads to unblock progress and reduce delays.
- Secure Document Upload & Versioning: IT and compliance teams can upload proposed policy drafts, risk assessment results, and security analysis reports. Cflow maintains version control, ensuring only the latest approved policy gets implemented and older drafts remain archived for traceability.
- Approval Path Transparency: Each step in the change process – from proposal to final sign-off is timestamped. All stakeholders can see who approved the change, when, and what conditions were applied. This transparency prevents unauthorized policy shifts and builds trust in governance.
- Mobile Access for Remote Teams: Stakeholders can initiate, approve, or monitor change requests from any device. Whether working from the office or remotely, teams stay aligned without delays caused by physical availability.
Get the best value for money with Cflow
User Roles & Permissions
IT Admin (Initiator)
- Responsibilities: Submit policy change request with reason, risk level, and proposed changes.
- Cflow Permission Level: Submit Form.
- Mapping: “IT Infrastructure” group.
Security Officer
- Responsibilities: Review encryption, storage location, and data access implications.
- Cflow Permission Level: Approve/Reject.
- Mapping: “IT Security” group.
Compliance Manager
- Responsibilities: Validate alignment with regulatory mandates and data protection laws.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Compliance” group.
Legal Counsel
- Responsibilities: Approve changes with contractual or legal impact.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Legal” group.
Audit Viewer
- Responsibilities: View historical policy changes and download reports for audit reviews.
- Cflow Permission Level: View Only.
- Mapping: “Audit Team” group.
Discover why teams choose Cflow
Form Design & Field Definitions
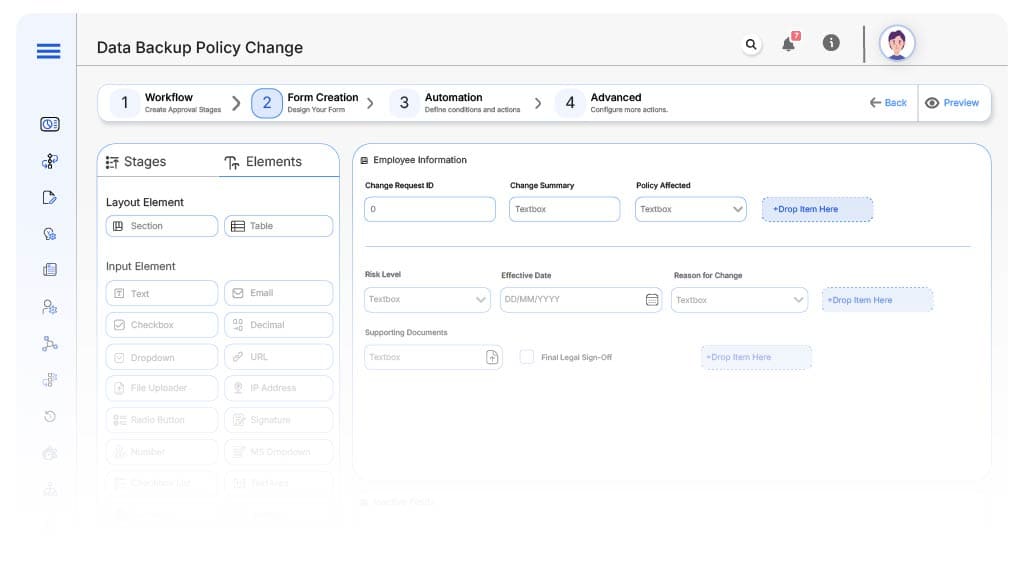
Field Label: Change Request ID
- Type: Autonumber
- Auto-Populate: on submission.
Field Label: Change Summary
- Type: Text Area
- Auto-Populate: Manual EntryType: Text Area
Field Label: Policy Affected
- Type: Dropdown (Backup Frequency, Storage Location, Encryption Standard, Retention Period, Others)
- Logic/Rules: Drives conditional routing
Field Label: Risk Level
- Type: Dropdown (Low, Medium, High)
- Logic/Rules: Medium/High routes to Risk Team
Field Label: Effective Date
- Type: Date Picker
- Logic/Rules: Cannot be a past date
Field Label: Reason for Change
- Type: Text Area
- Logic/Rules: Required
Field Label: Supporting Documents
- Type: File Upload
- Logic/Rules: Required for Medium/High risk
Field Label: IT Security Notes
- Type: Text Area
- Logic/Rules: Visible only to Security role
Field Label: Compliance Comments
- Type: Text Area
- Logic/Rules: Required for Compliance role
Field Label: Final Legal Sign-Off
- Type: Checkbox
- Logic/Rules: Mandatory if Policy Affected = Legal
Field Label: Archive Confirmation
- Type: Checkbox
- Logic/Rules: Required for IT Admin before closure
Transform your Workflow with AI fusion
Approval Flow & Routing Logic
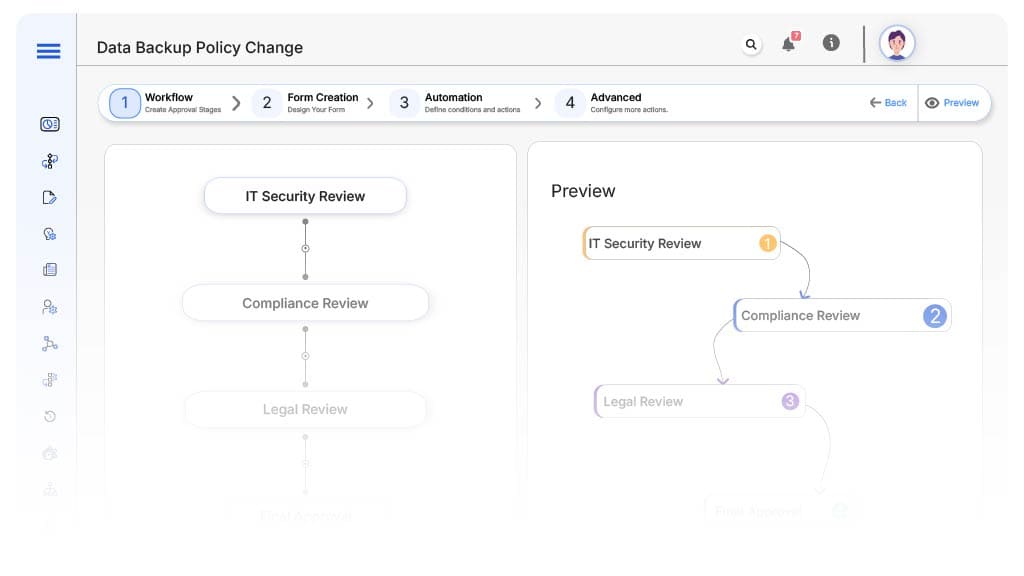
Submission → IT Security Review
- Status Name: Pending Security Review
- Notification Template: “Hi Security, a backup policy change needs your review. Please validate encryption/storage changes.”
- On Approve: Routes to Compliance Manager
IT Security → Compliance Review
- Status Name: Pending Compliance Review
- Notification Template: “Hi Compliance, review the request to ensure alignment with regulatory standards.”
- Escalation: Reminder after 2 days
- On Approve: Routes to Legal (if flagged)
Compliance → Legal Review (Conditional)
- Status Name: Pending Legal Review
- Notification Template: “Hi Legal, your sign-off is required on this policy change request.”
- On Approve: Moves to IT Finalization
Legal → IT Finalization
- Status Name: Pending Final IT Update
- Notification Template: “Hi IT Admin, please update the backup policy and confirm archiving.”
- On Approve: Status changes to Complete
Final → Change Completed
- Status Name: Policy Change Complete
- Notification Template: “Backup Policy Change fully approved and implemented. Record archived in audit logs.”
Transform your AI-powered approvals
Implementation Steps in Cflow
Create a new workflow
Design the form
Set up User Roles/Groups
Build flow
Configure notifications
Apply logic
Publish workflow
Test flow
Adjust logic
Go live
Example Journey: Maria’s Backup Policy Update
FAQ's
Unleash the full potential of your AI-powered Workflow

