- Cflow
- Incident Response Plan Automation
Incident Response Plan Automation

Clow Team

A well-executed incident response plan (IRP) is vital for mitigating security breaches, data leaks, and operational disruptions. However, most organizations still rely on manual checklists and siloed communication during incidents, leading to delayed responses, regulatory violations, and reputational damage. Research shows that 60% of companies experience avoidable damage due to uncoordinated response efforts.
Without automation, IT, security teams, compliance officers, and executives struggle to initiate timely actions, track containment steps, and document post-incident reviews. This guide explains how Cflow automates every stage of the Incident Response Plan, from incident identification to resolution and closure.
What Is Incident Response Plan Process?
The Incident Response Plan Process defines how an organization detects, assesses, contains, and resolves security incidents or operational disruptions in a structured, time-sensitive manner.
IRPs are essential for minimizing damage, restoring services, and ensuring regulatory compliance.
Think of each incident as a coordinated emergency operation—where every role, task, and timeline must be defined, tracked, and auditable.
Research shows that automating IRPs cuts average response time by 55% and reduces regulatory fines by up to 30%.
Why Incident Response Plan Automation Matters for Organizations
Faster Containment
Consistency in Execution
Risk Reduction
Improved Collaboration
Audit-Ready Logs
Key Benefits of Automating Incident Response Plans with Cflow
- Incident Trigger & Categorization: Cflow allows automated triggers based on severity level, threat type, or source system. Incidents are categorized instantly, ensuring appropriate containment and notification steps are taken without delay. This minimizes response latency and ensures teams are activated before damage spreads.
- Role-Based Action Assignment: Once an incident is logged, Cflow routes containment and investigation tasks to assigned owners based on incident type. This ensures accountability and reduces confusion during critical moments. Custom roles and fallback assignees ensure no step is missed during peak load.
- Real-Time Alerts & Escalations: Automated alerts notify relevant teams instantly. Escalations occur when SLA deadlines are missed, ensuring that high-priority incidents don’t get buried under manual coordination. Alerts are fully configurable, supporting email, SMS, and in-app channels.
- Documentation & Compliance Enforcement: Cflow mandates attachment of evidence, logs, and action summaries for each response stage. Legal and compliance teams are alerted if documentation or review is incomplete.This enforces audit-readiness and reduces non-compliance penalties during investigations.
- Post-Incident Review & Lessons Learned: Automates the post-incident review process with structured inputs from stakeholders. This helps organizations analyze root causes and improve future preparedness. Recurring patterns and system gaps are flagged automatically for leadership action.
- Executive Dashboards & Mobile Access: Leadership can monitor incident status, approve actions, or sign off from anywhere. Real-time dashboards ensure transparency across all stakeholders. Mobile-friendly access supports remote response management during after-hours or travel.
Get the best value for money with Cflow
User Roles & Permissions
IT Security Analyst (Initiator)
- Responsibilities: Log the incident with severity level, impact analysis, and logs.
- Cflow Permission Level: Submit Form
- Mapping: “Security Team”
Incident Manager
- Responsibilities: Validate incident scope, assign response actions, and coordinate containment.
- Cflow Permission Level: Approve/Reject
- Mapping: “IT Operations”
Compliance Officer
- Responsibilities: Ensure actions align with legal and regulatory standards.
- Cflow Permission Level: Approve/Reject
- Mapping: “Compliance Team”
Legal Counsel
- Responsibilities: Review data breach implications, disclosure obligations, and legal risk.
- Cflow Permission Level: Approve/Reject
- Mapping: “Legal Group”
CISO / CIO (Final Reviewer)
- Responsibilities: Provide executive-level oversight and closure approval.
- Cflow Permission Level: Approve/Reject
- Mapping: “Executive Board”
Discover why teams choose Cflow
Form Design & Field Definitions
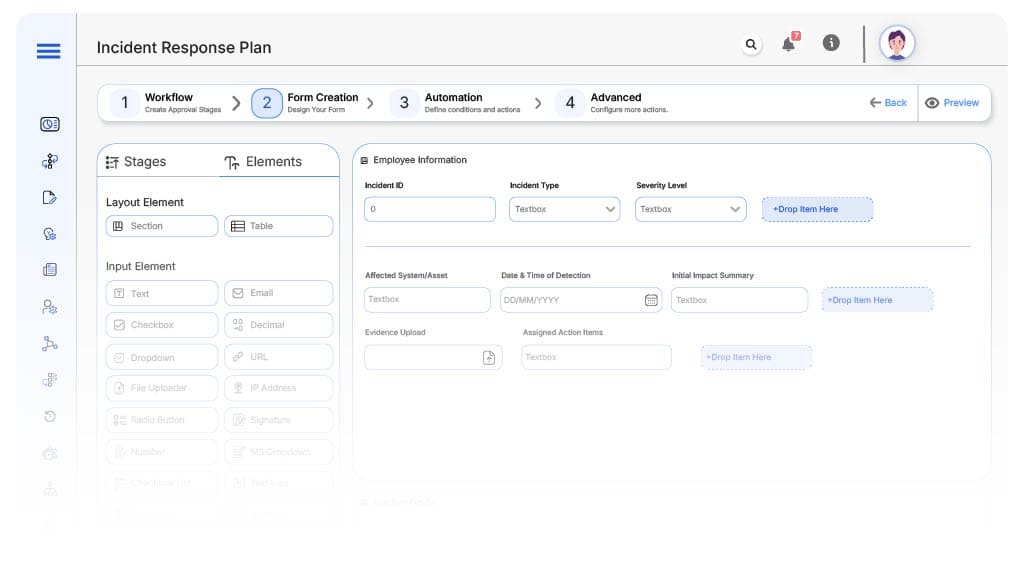
Field Label: Incident ID
- Type: Autonumber
- Auto-Populate: Generated on submission.
Field Label: Incident Type
- Type: Dropdown (Data Breach, Downtime, Unauthorized Access, Malware, Others)
- Logic/Rules: Drives routing logic
Field Label: Severity Level
- Type: Dropdown (Low, Medium, High, Critical)
- Logic/Rules: Routes to escalation if high/critical
Field Label: Affected System/Asset
- Type: Text
- Logic/Rules: Mandatory
Field Label: Date & Time of Detection
- Type: Date-Time Picker
- Logic/Rules: Required
Field Label: Initial Impact Summary
- Type: Text Area
- Logic/Rules: Required
Field Label: Evidence Upload
- Type: File Upload
- Logic/Rules: Required for critical incidents
Field Label: Assigned Action Items
- Type: Text Area
- Logic/Rules: Editable by Incident Manager
Field Label: Compliance Notes
- Type: Text Area
- Logic/Rules: Required if data breach involved
Field Label: Legal Observations
- Type: Text Area
- Logic/Rules: Required for disclosure cases
Field Label: Executive Sign-Off
- Type: Checkbox
- Logic/Rules: Completion confirmation
Transform your Workflow with AI fusion
Approval Flow & Routing Logic
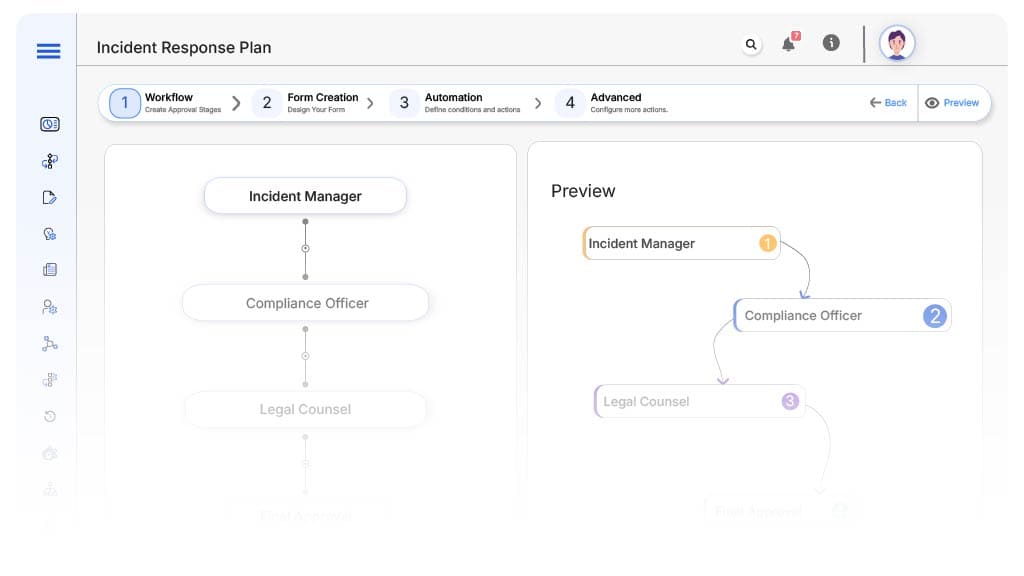
Submission → Incident Manager
- Status Name: Pending Incident Validation
- Notification: “New incident logged. Review scope and assign response.”
- On Approve: Moves to Compliance Officer
- On Reject: Returns to Security Analyst
- Escalation: After 2 hours
Incident Manager → Compliance Officer
- Status Name: Pending Compliance Review
- Notification: “Please review incident response for compliance alignment.”
- On Approve: Moves to Legal
- On Reject: Returns to Incident Manager
- Escalation: After 4 hours
Compliance Officer → Legal Counsel (if breach/disclosure required)
- Status Name: Pending Legal Review
- Notification: “Incident needs legal assessment and documentation.”
- On Approve: Moves to Executive
- On Reject: Returns to Compliance
- Escalation: After 1 day
Legal → CISO/CIO
- Status Name: Pending Executive Sign-Off
- Notification: “Review incident closure and endorse resolution.”
- On Approve: Status marked Resolved
- On Reject: Returns to Legal
- Escalation: After 1 day
Final → Resolved
- Status Name: Incident Closed
- Notification: “Incident response complete. Review lessons learned and archive.”
Transform your AI-powered approvals
Implementation Steps in Cflow
Create a new workflow
Design the form
Assign roles
Build approval flow
Set escalation rules
Integrate with ITSM or alerting system
Test scenarios
Go live
Example Journey: Incident Response Execution in Cflow
FAQ's
Unleash the full potential of your AI-powered Workflow

