- Cflow
- Security Patch Deployment Automation
Security Patch Deployment Automation

Clow Team

Security patch deployment is essential for protecting systems against known vulnerabilities, malware, and zero-day threats. Without automation, manual patching often leads to delayed updates, exposed systems, and compliance failures. Recent industry research shows that 57% of data breaches result from unpatched known vulnerabilities.
Without automation, IT teams, security officers, compliance teams, and leadership struggle to coordinate patch scheduling, validate patch applicability, monitor success, and maintain audit trails. This guide walks you through exactly how Cflow automates Security Patch Deployment Process, from patch proposal to full deployment sign-off.
What Is Security Patch Deployment Process?
The Security Patch Deployment Process governs how software updates, security fixes, and firmware patches are identified, tested, approved, and rolled out to production environments while ensuring business continuity and compliance.
Think of security patching like regular vaccine updates , every patch requires prioritization, risk evaluation, staged deployment, and thorough verification.
Recent industry research shows that automating patch deployment reduces vulnerability windows by 60% and improves patch success rates by 75%.
Why Security Patch Deployment Matters for Organizations
Vulnerability Mitigation
Regulatory Compliance
Business Continuity
Audit Trail
Key Benefits of Automating Security Patch Deployment with Cflow
- Centralized Patch Request Portal: Cflow offers a unified portal where IT and security teams log patch requests with full vulnerability, vendor, and system details. This eliminates email chains and ensures all patch metadata is captured accurately from the start. It streamlines submissions and sets the stage for efficient, policy-driven approvals.
- Dynamic Routing Based on Severity: Cflow intelligently routes patch requests based on CVSS scores, system criticality, and business impact. High-risk vulnerabilities are escalated, while routine patches follow standard review paths.This prioritization ensures urgent issues get immediate attention without overwhelming approvers.
- Multi-Level Approval Workflows: Patch requests flow through tiered approvals – IT, security, compliance, and executives based on risk and scope. Each stakeholder signs off at the right stage, improving oversight and accountability. This layered workflow supports internal controls and regulatory mandates.
- Real-Time Notifications & Escalations: Automated alerts keep teams informed of pending approvals, overdue actions, or missed deadlines. Escalation rules kick in for unresolved high-risk items, ensuring nothing falls through the cracks. This reduces patch delays and minimizes exposure windows.
- Testing & Rollback Plans: Cflow mandates testing in sandbox environments and requires rollback documentation before deployment. IT teams must validate patch stability, compatibility, and risk mitigation in staging. This reduces service disruptions and supports safer change control.
- Full Audit Trail & Patch History: Every step—submission, review, testing, approval, deployment – is logged for compliance and audits. Cflow’s searchable records ensure traceability of decisions and changes made. Auditors and IT managers can verify patch histories with ease.
Get the best value for money with Cflow
User Roles & Permissions
Security Analyst (Initiator)
- Responsibilities: Submit patch deployment request with vulnerability details, CVSS score, and vendor advisories.
- Cflow Permission Level: Submit Form.
- Mapping: “Security Team” group.
IT Administrator
- Responsibilities: Validate technical compatibility, deployment readiness, and impact on production systems.
- Cflow Permission Level: Approve/Reject.
- Mapping: “IT Operations” group.
Compliance Officer (Conditional)
- Responsibilities: Verify regulatory timelines and standards adherence for patch cycles.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Compliance Team” group.
IT Security Manager
- Responsibilities: Final technical review, assess risk scoring, and validate vulnerability closure.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Security Leadership” group.
Executive Leadership (Conditional)
- Responsibilities: Final sign-off for critical system or downtime-sensitive patches.
- Cflow Permission Level: Approve/Reject.
- Mapping: “IT Leadership” group.
Discover why teams choose Cflow
Form Design & Field Definitions
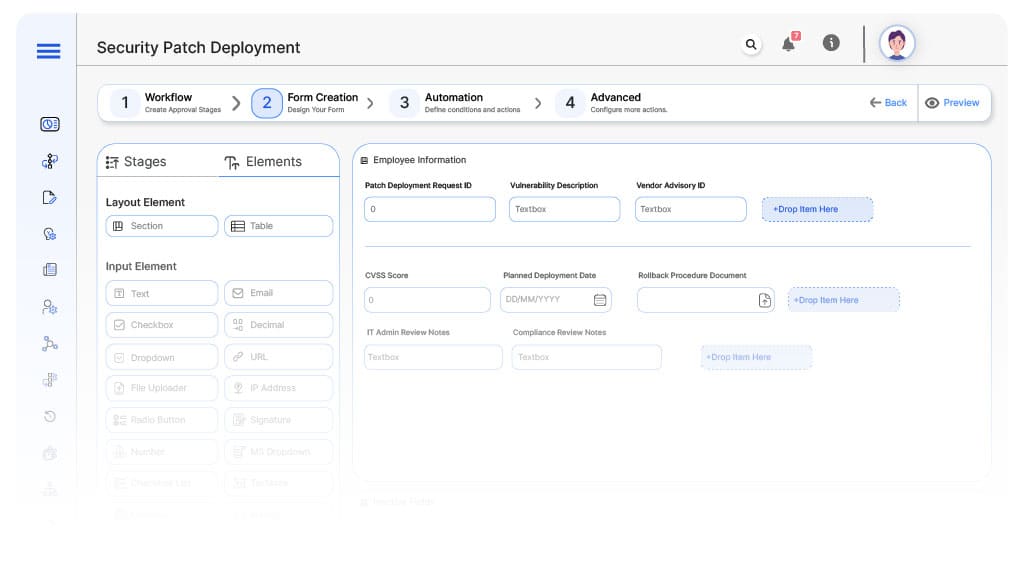
Field Label: Patch Deployment Request ID
- Type: Autonumber
- Auto-Populate: Generated on submission.
Field Label: Vulnerability Description
- Type: Text Area
- Logic/Rules: Mandatory.
Field Label: Vendor Advisory ID
- Type: Text
- Logic/Rules: Mandatory.
Field Label: CVSS Score
- Type: Numeric Field 0–10)
- Logic/Rules: Drives routing.
Field Label: Affected Systems List
- Type: Repeater (System Name, Environment, OS Version)
- Logic/Rules: Mandatory.
Field Label: Planned Deployment Date
- Type: Date Picker
- Logic/Rules: Mandatory.
Field Label: Test Environment Results
- Type: File Upload
- Logic/Rules: Mandatory for IT review.
Field Label: Rollback Procedure Document
- Type: File Upload
- Logic/Rules: Mandatory.
Field Label: IT Admin Review Notes
- Type: Text Area
- Logic/Rules: Required for IT administrator.
Field Label: Compliance Review Notes
- Type: Text Area
- Logic/Rules: Required for compliance officer.
Field Label: Security Manager Notes
- Type: Text Area
- Logic/Rules: Required for security manager.
Field Label: Executive Comments
- Type: Text Area
- Logic/Rules: Required for executive approval.
Field Label: Deployment Confirmation
- Type: Checkbox
- Logic/Rules: IT Admin marks patch applied.
Transform your Workflow with AI fusion
Approval Flow & Routing Logic
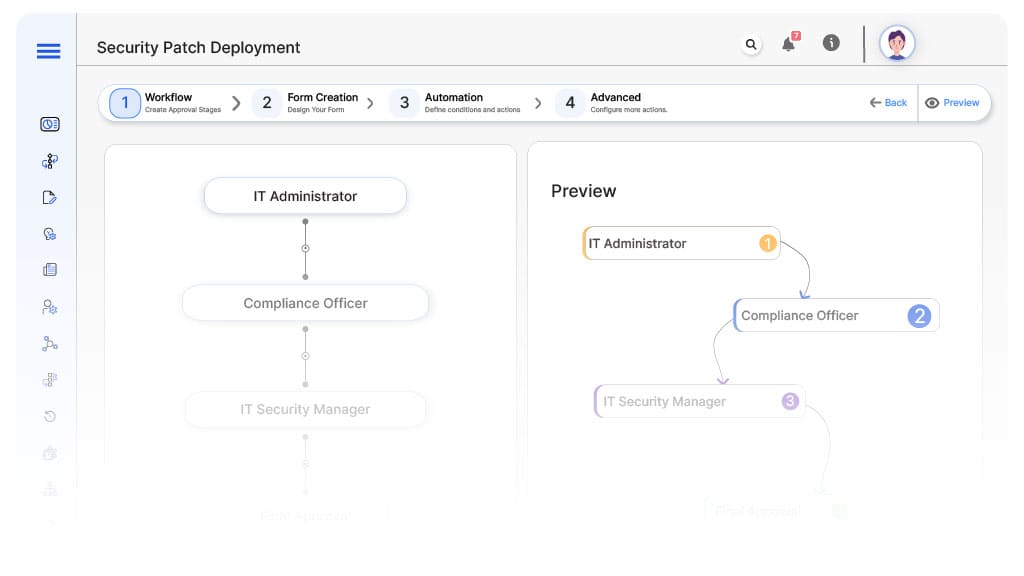
Submission → IT Administrator
- Status Name: Pending IT Review
- Notification Template: “Hi IT, new patch deployment request submitted for validation.”
- On Approve: Moves to Compliance Officer (if applicable).
- On Reject: Returns to Security Analyst.
- Escalation: Reminder after 1 day.
IT → Compliance Officer (Conditional)
- Status Name: Pending Compliance Review
- Notification Template: “Hi Compliance, patch request requires regulatory validation.”
- On Approve: Moves to Security Manager.
- On Reject: Returns to IT Administrator.
- Escalation: Reminder after 1 day.
Compliance → IT Security Manager
- Status Name: Pending Security Manager Review
- Notification Template: “Hi Security Manager, patch request ready for risk approval.”
- On Approve: Moves to Executive Leadership (if applicable).
- On Reject: Returns to Compliance Officer.
- Escalation: Reminder after 1 day.
Security → Executive Leadership (Conditional)
- Status Name: Pending Executive Approval
- Notification Template: “Hi Leadership, high-risk patch requires final sign-off.”
- On Approve: Moves to Deployment Authorized.
- On Reject: Returns to Security Manager.
- Escalation: Reminder after 1 day.
Final → Deployment Authorized
- Status Name: Patch Approved for Deployment
- Notification Template: “Patch fully approved and scheduled for deployment.”
Transform your AI-powered approvals
Implementation Steps in Cflow
Create a new workflow
Design the form
Set up User Roles/Groups
Build the process flow diagram
Configure notifications
Apply templates and escalation rules per Approval Flow.
Set conditional logic
Save and publish workflow
Activate process.
Test with a sample request
Adjust logic if needed
Go live
Example Journey: Critical Windows Server Patch
FAQ's
Setup typically completes within 5–7 business days.
Unleash the full potential of your AI-powered Workflow

