- Cflow
- Network Configuration Update Automation
Network Configuration Update Automation

Clow Team

Network configuration updates are critical for maintaining secure, stable, and optimized IT infrastructure. Without automation, manual configuration change requests often lead to outages, security vulnerabilities, and compliance failures. Recent industry research shows that 65% of network incidents are caused by improper configuration changes.
Without automation, IT teams, network engineers, security officers, and leadership struggle to validate change requests, enforce change controls, and track approvals. This guide walks you through exactly how Cflow automates Network Configuration Update Process, from request submission to change implementation.
What Is Network Configuration Update Process?
The Network Configuration Update Process governs how IT teams request, review, approve, and implement changes to routers, switches, firewalls, and other network components while ensuring business continuity and compliance.
Think of configuration updates like surgical adjustments to the network’s backbone; every change requires clear justification, risk evaluation, multi-level approvals, and full documentation.
Recent industry research shows that automating network configuration updates reduces unplanned downtime by 55% and improves change success rates by 70%.
Why Network Configuration Updates Matter for Organizations
Business Continuity
Security Compliance
Audit Readiness
Change Control
Key Benefits of Automating Network Configuration Update Process with Cflow
- Centralized Configuration Request Portal: Cflow centralizes all network configuration requests through a structured form. IT teams can log, track, and route updates across routers, switches, and firewalls. This eliminates scattered emails and ensures every change begins with proper documentation. It improves visibility, traceability, and control.
- Conditional Routing by Device Type or Risk: Requests are dynamically routed based on device type, change severity, or compliance risk. High-risk changes can be escalated to security or compliance teams, while low-risk updates follow standard IT review. This targeted approach reduces delays and improves governance without adding friction.
- Multi-Team Collaboration & Parallel Tasks: Network updates often require coordination between IT, security, and operations. Cflow supports parallel task assignments and cross-functional approvals to speed up execution. Teams work simultaneously, and the process doesn’t wait for sequential sign-offs. This shortens update cycles and avoids miscommunication.
- Audit Trail & Version Control: Every configuration change is logged with a timestamp, approver details, and version history. Cflow ensures rollback paths are documented, and compliance teams have full visibility. It simplifies audit readiness and tracks accountability across the lifecycle of every update.
- Automated Notifications & Escalations: Cflow alerts stakeholders at each stage—from submission to final approval. If an action is delayed, escalation rules notify higher authorities automatically. This ensures nothing slips through the cracks and time-sensitive changes are never stalled in inboxes.
- Role-Based Access & Permissions: Access is restricted based on user roles, ensuring only authorized personnel can initiate, view, or approve network changes. IT admins, security officers, and compliance managers operate within their defined scopes. This enhances control, reduces risk, and maintains data integrity.
- Integration with Network Monitoring Tools: Cflow integrates with NMS or configuration management tools to push approved updates and sync status. This ensures live environments reflect approved configurations without manual entry. It reduces duplication, errors, and brings real-time alignment between approval and execution.
Get the best value for money with Cflow
User Roles & Permissions
Requesting Network Engineer (Initiator)
- Responsibilities: Submit configuration update request with system details, change description, and rollback plan.
- Cflow Permission Level: Submit Form.
- Mapping: “Network Team” group.
Network Engineering Lead
- Responsibilities: Validate technical feasibility, network impact, and change completeness.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Network Leadership” group.
IT Security Officer
- Responsibilities: Review security implications, access control updates, and vulnerability risks.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Security Team” group.
Procurement Officer
- Responsibilities: Verify compliance with regulatory frameworks such as PCI-DSS, HIPAA, or ISO.
- Cflow Permission Level: Approve/Reject.
- Mapping: “Compliance Team” group.
IT Director (Conditional)
- Responsibilities: Final sign-off for high-risk or critical infrastructre updates.
- Cflow Permission Level: Approve/Reject.
- Mapping: “IT Leadership” group.
Discover why teams choose Cflow
Form Design & Field Definitions
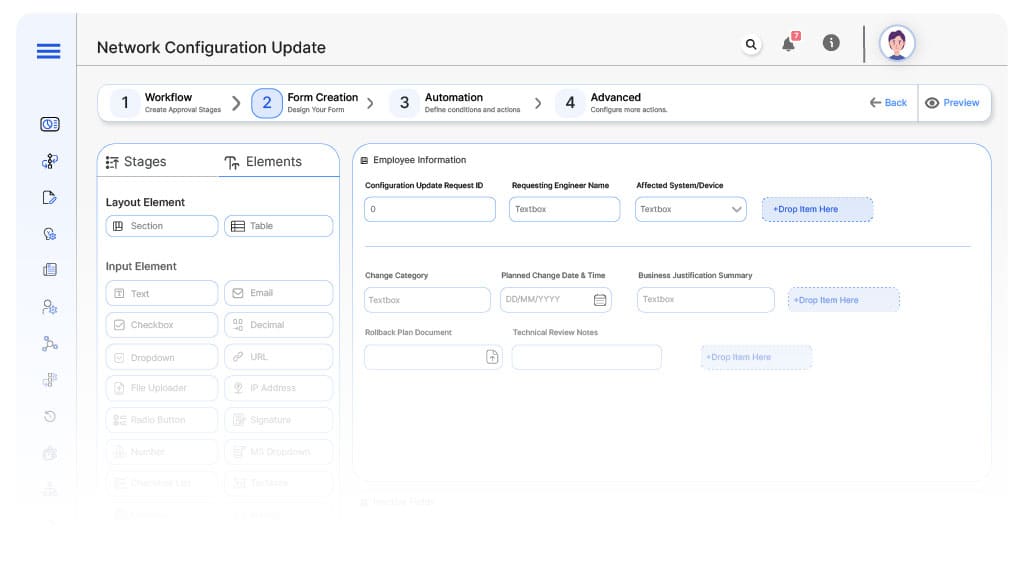
Field Label: Configuration Update Request ID
- Type: Autonumber
- Auto-Populate: Generated on submission.
Field Label: Requesting Engineer Name
- Type: Text (Autofill)
- Auto-Populate: From user profile.
Field Label: Affected System/Device
- Type: Dropdown
- Logic/Rules: Mandatory.
Field Label: Change Category
- Type: Dropdown (Firewall Rule Change, VLAN Update, Routing Table Update, Access Control, Software Patch, Firmware Upgrade)
- Logic/Rules: Drives routing.
Field Label: Planned Change Date & Time
- Type: DateTime Picker
- Logic/Rules: Mandatory.
Field Label: Business Justification Summary
- Type: Text Area
- Logic/Rules: Mandatory.
Field Label: Rollback Plan Document
- Type: File Upload
- Logic/Rules: Mandatory.
Field Label: Technical Review Notes
- Type: Text Area
- Logic/Rules: Required for network lead.
Field Label: Security Review Notes
- Type: Text Area
- Logic/Rules: Required for security officer.
Field Label: Compliance Review Notes
- Type: Text Area
- Logic/Rules: Required for compliance officer.
Field Label: IT Director Comments
- Type: Text Area
- Logic/Rules: Required for IT director.
Field Label: Change Implementation Confirmation
- Type: Checkbox
- Logic/Rules: Marked after change is applied
Transform your Workflow with AI fusion
Approval Flow & Routing Logic
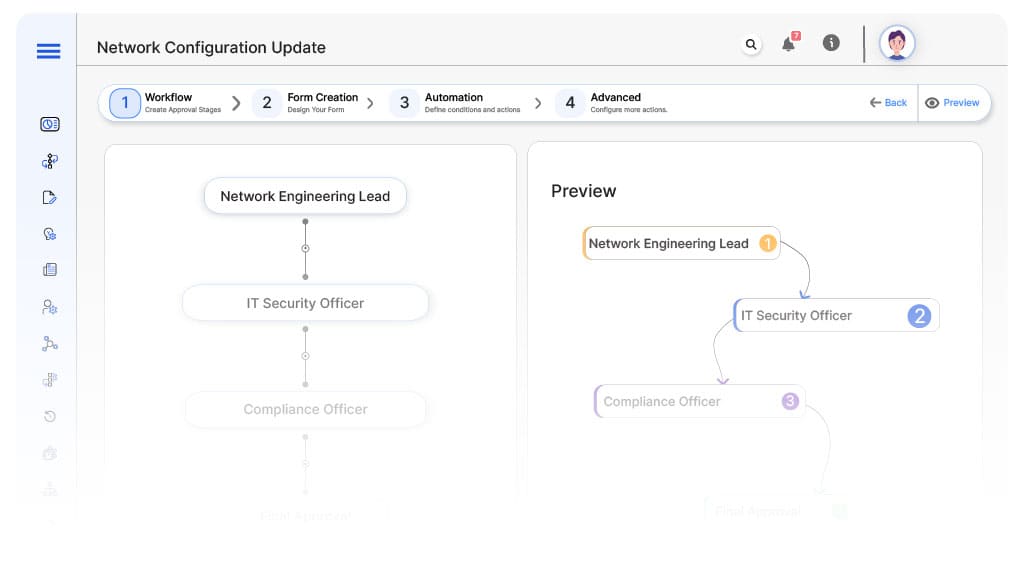
Submission → Network Engineering Lead
- Status Name: Pending Technical Review
- Notification Template: “Hi Network Lead, new configuration update request submitted for review.”
- On Approve: Moves to IT Security Officer.
- On Reject: Returns to Requesting Engineer.
- Escalation: Reminder after 1 day.
Network Lead → IT Security Officer
- Status Name: Pending Security Review
- Notification Template: “Hi Security, network update request requires risk review.”
- On Approve: Moves to Compliance Officer (if applicable).
- On Reject: Returns to Network Lead.
- Escalation: Reminder after 1 day.
Security → Compliance Officer (Conditional)
- Status Name: Pending Compliance Review
- Notification Template: “Hi Compliance, configuration update requires regulatory validation.”
- On Approve: Moves to IT Director (if applicable).
- On Reject: Returns to Security Officer.
- Escalation: Reminder after 1 day.
Compliance → IT Director (Conditional)
- Status Name: Pending IT Director Approval
- Notification Template: “Hi Director, high-risk configuration change requires final sign-off.”
- On Approve: Moves to Change Authorized.
- On Reject: Returns to Compliance Officer.
- Escalation: Reminder after 1 day.
Final → Change Authorized
- Status Name: Change Fully Approved
- Notification Template: “Configuration update approved and ready for implementation.”
Final → Procurement Closed
- Status Name: Change Fully Approved
- Notification Template: “Configuration update approved and ready for implementation.”
Transform your AI-powered approvals
Implementation Steps in Cflow
Create a new workflow
Design the form
Set up User Roles/Groups
Build the process flow diagram
Configure notifications
Apply templates and escalation rules per Approval Flow.
Set conditional logic
Save and publish workflow
Activate process.
Test with a sample request
Adjust logic if needed
Go live
Example Journey: Firewall Rule Update
FAQ's
Unleash the full potential of your AI-powered Workflow

