- Cflow
- IT Risk Assessment Automation
IT Risk Assessment Automation

Clow Team

Purchasing a domain name may seem like a simple task, but in most organizations, it involves multiple approvals, cross-team coordination, vendor validations, and compliance checks. Without automation, this process often gets delayed by email chains, unclear ownership, and a lack of budget tracking, causing missed opportunities or inconsistent domain management.
Cflow eliminates this chaos by automating the Domain Name Purchase process end-to-end. From request initiation by Marketing or IT to approvals, vendor selection, and domain activation, every step is governed by structured workflows, ensuring visibility, accountability, and compliance.
What is IT Risk Assessment Automation?
The Domain Name Purchase Process refers to the internal request, approval, and procurement lifecycle for registering and managing domain names for an organization. It ensures domain purchases align with branding, security, and IT policies.
Imagine a marketing team needing a new domain for a product campaign. Without a structured process, they may buy domains without IT review or budget tracking, leading to fragmentation, renewals missed, or even duplicate purchases.
According to a TechRepublic study, nearly 48% of enterprise domain purchases lack centralized oversight, leading to unmanaged renewals and security risks.
Why Automate IT Risk Assessments?
Real-Time Visibility
Policy Enforcement
Cross-Functional Collaboration
Audit Trail
Faster Remediation
Key Benefits of IT Risk Assessment Automation with Cflow
- Centralized Risk Register: All risk submissions, responses, and approvals are tracked in one centralized system with audit-friendly logs. Access is role-based, ensuring the right stakeholders view or update risks at the appropriate stage. This eliminates data fragmentation and improves transparency across IT and compliance teams.
- Automated Risk Categorization: Cflow automatically assigns severity and priority tags based on asset type, likelihood, and impact level. High-risk items are escalated immediately, while low-priority risks are tracked for scheduled review. This automation reduces manual sorting errors and accelerates decision-making.
- Multi-Level Review Workflow: Each risk follows a structured workflow involving IT, Security, Compliance, and Leadership, based on criticality. Steps are sequenced with notifications and SLA-based escalations to avoid delays. This ensures proper risk ownership and accountability at every level.
- Mitigation Planning & Tracking: Risks include mitigation plans with task assignments, deadlines, and progress tracking in real time. Cflow alerts stakeholders of upcoming or overdue mitigation deadlines automatically. This ensures risks are not just logged, but actively managed until closure.
- Compliance Mapping: Each risk can be mapped to regulatory standards like ISO 27001, SOC 2, HIPAA, or internal controls. Compliance teams can cross-reference risks with audit categories or unresolved issues. This ensures a proactive compliance posture and speeds up reporting.
- Real-Time Reporting: Dashboards display unresolved risks, SLA breaches, mitigation progress, and category breakdowns. Executives and IT leads can filter views based on time, department, or severity. This facilitates quick, informed decision-making and oversight.
- Mobile Access for Review: Users can submit, review, or escalate risks from mobile devices with secure login and role access. Field teams and traveling managers stay in the loop without delay. This flexibility improves responsiveness and maintains risk governance continuity.
Get the best value for money with Cflow
User Roles & Permissions
IT Analyst
- Responsibilities: Submit new risks, document impact, propose initial control actions.
- Permission: Submit Form
- Group: “IT Analysts”
Security Lead
- Responsibilities: Validate threat severity, recommend mitigation strategies.
- Permission: Task Owner
- Group: “Security Team”
Compliance Officer
- Responsibilities: Map risks to controls, validate compliance alignment.
- Permission: Task Owner
- Group: “Compliance”
IT Manager
- Responsibilities: Approve or reject proposed mitigation plans.
- Permission: Approve
- Group: “IT Management”
CIO / Leadership
- Responsibilities: Final review for high-impact risks.
- Permission: Approve
- Group: “Leadership”
Discover why teams choose Cflow
Form Design & Field Definitions
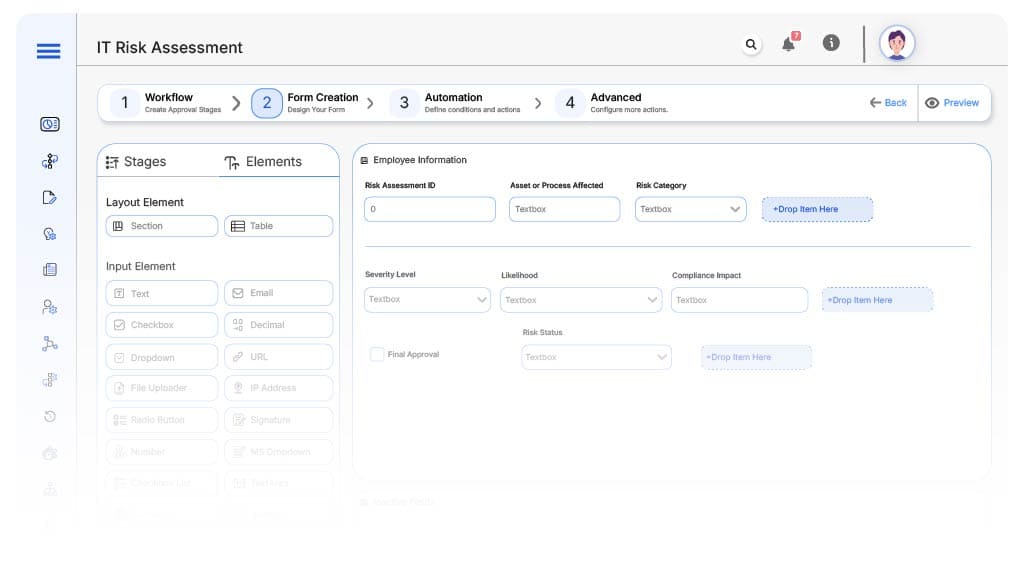
Field Label: Risk Assessment ID
- Type: Autonumber
- Auto-Populate: Generated on submission
Field Label: Asset or Process Affected
- Type: Text
- Logic/Rules: Required
Field Label: Risk Category
- Type: Dropdown (Data Loss, Malware, Unauthorized Access, Downtime, Others)
- Logic/Rules: Determines risk handling team and routing path
Field Label: Severity Level
- Type: Dropdown (Low, Medium, High, Critical)
- Logic/Rules: Drives routing urgency and escalation
Field Label: Likelihood
- Type: Dropdown (Rare, Unlikely, Likely, Certain)
- Logic/Rules: Required to calculate overall risk impact
Field Label: Compliance Impact
- Type: Multi-select (ISO 27001, SOC 2, HIPAA, GDPR)
- Logic/Rules: Tags risks affecting regulatory requirements
Field Label: Initial Risk Description
- Type: Text Area
- Logic/Rules: Mandatory for every submission
Field Label: Suggested Mitigation Plan
- Type: Text Area
- Logic/Rules: Optional for analysts, reviewed in later stages
Field Label: Risk Status
- Type: Dropdown (Open, Under Review, Mitigated, Accepted, Deferred)
- Logic/Rules: Updated throughout the risk lifecycle
Field Label: Final Approval
- Type: Checkbox
- Logic/Rules: Checked only by CIO/Leadership for closure
Transform your Workflow with AI fusion
Approval Flow & Routing Logic
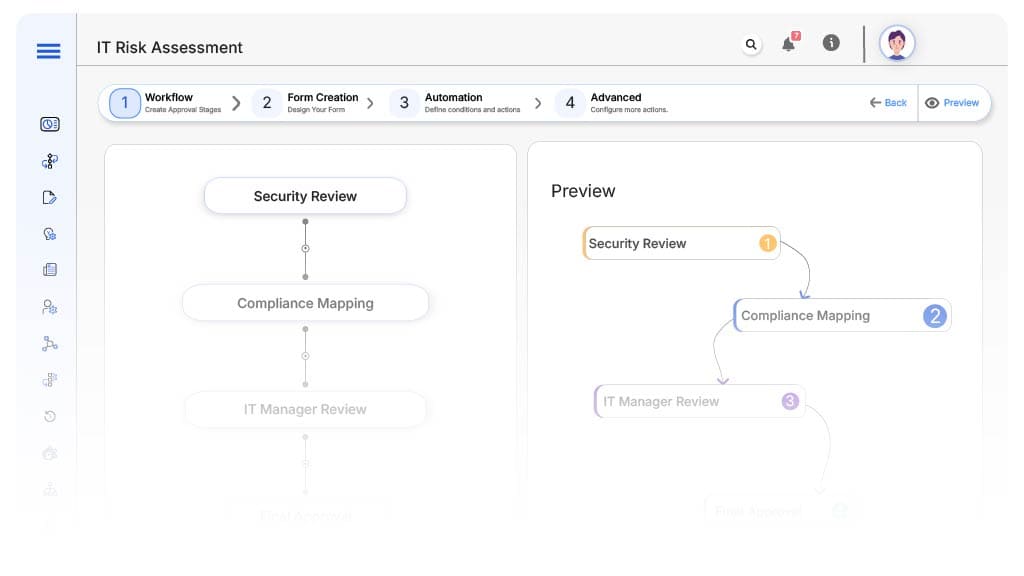
Submission → Security Review
- Status: Pending Threat Review
- Notification: “Security team, a new IT risk has been logged. Please validate severity and suggest actions.”
Security → Compliance Mapping
- Status: Compliance Mapping
- Notification: “Compliance, assess regulatory implications of the identified risk.”
- Escalation: 2-day reminder
Compliance → IT Manager Review
- Status: Manager Review
- Notification: “IT Manager, review and approve the mitigation plan.”
- Escalation: 2-day reminder
IT Manager → CIO Review (if Critical)
- Status: Final Approval
- Notification: “Leadership, critical risk pending your approval or escalation.”
Final → Risk Closed or Deferred
- Status: Resolution Logged
- Notification: “Risk has been resolved/accepted. Full trail archived for audit.”
Transform your AI-powered approvals
Implementation Steps in Cflow
Create a new workflow
Design the form
Set Up User Groups
Build Routing Logic
Configure Alerts
Test the Workflow
Train Stakeholders
Go Live
Example Scenario: Cloud Access Misconfiguration
FAQ's
Unleash the full potential of your AI-powered Workflow

