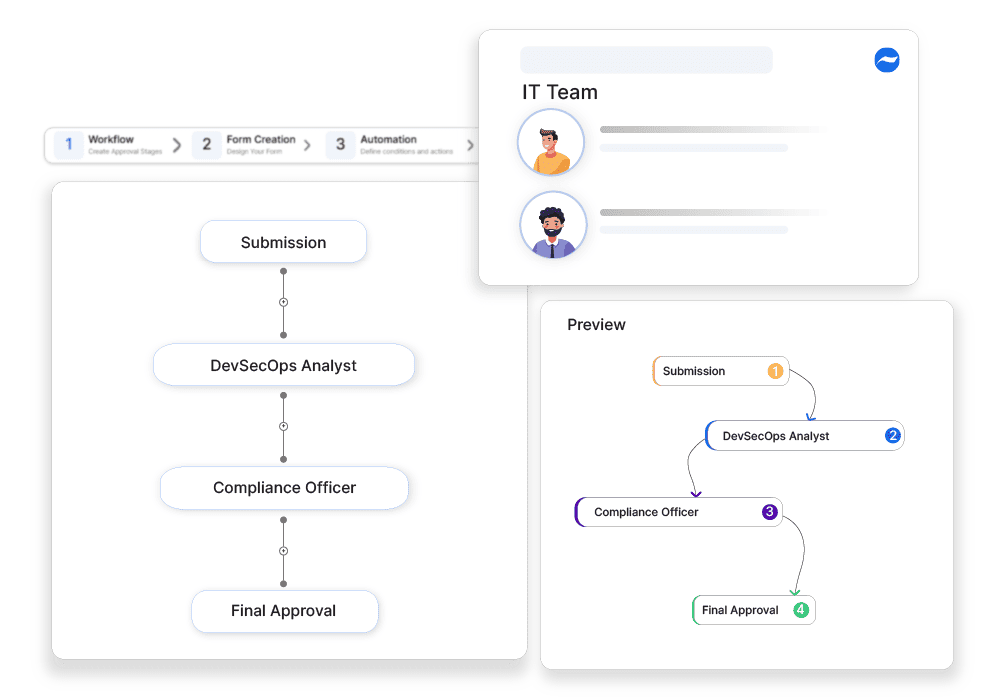
Container Security Policy Enforcement Process
Why automate?
How Cflow Helps:
Approval-Based Security Policy Updates
Cflow ensures that all container security modifications go through structured approvals, preventing unauthorized access.
Compliance with Security Frameworks
Approved policies align with CIS benchmarks and DevSecOps best practices, ensuring protection.
Faster Response to Security Threats
Critical security updates receive priority approvals, minimizing exposure to container vulnerabilities.
Full Audit Trail for Security Policy Changes
Cflow logs all approved security updates, enabling IT teams to track policy enforcement history.
Frequently Asked Questions
What is a container security policy enforcement process?
A process for defining and enforcing security rules for containerized applications.
What are the main challenges in container security policy enforcement?
Inconsistent security settings, misconfigured policies, and runtime vulnerabilities.
How can businesses streamline container security policy enforcement?
By automating policy enforcement, using container security platforms, and setting real-time alerts for breaches.